February 2009 - Vol. 52 No. 2

Features
Seven Principles For Secure E-Voting
Economic and Business Dimensions: The Extent of Globalization of Software Innovation
Human Computing Skills: Rethinking the K-12 Experience
International Communications Tapped For Intelligence-Gathering
Inside Risks: U.S. Election After-Math
Point/Counterpoint: Network Neutrality Nuances
Parallel Programming with Transactional Memory
Improving Performance on the Internet
Compiler Research: The Next 50 Years
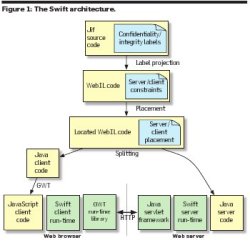
Technical Perspective: Tools For Information to Flow Securely and Swift-ly
Building Secure Web Applications With Automatic Partitioning
Technical Perspective: The Complexity of Computing Nash Equilibrium
The Complexity of Computing a Nash Equilibrium
Puzzled: Will My Algorithm Terminate?
Networks of Contextualized Data: a Framework For Cyberinfrastructure Data Management
For Sale By Owner Online: Who Gets the Saved Commission?
Oracle, Where Shall I Submit My Papers?
Automatically Profiling the Author of an Anonymous Text
Shadow Systems: the Good, the Bad and the Ugly
Why Is Management Is In Trouble and How to Save It: Lessons Learned in the Automotive Industry
Why File Sharing Networks Are Dangerous?
Technical Opinion: Multitasking With Laptops During Meetings