Ensuring Transparency in Computational Modeling
Research and Advances
Open Access Publishing in Science
Who Captures Value in a Global Innovation Network?: The Case of Apple's iPod
Concept Similarity By Evaluating Information Contents and Feature Vectors: A Combined Approach
Technical Opinion: Security Threats of Smart Phones and Bluetooth
Compiler Research: The Next 50 Years
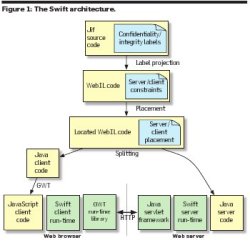
Technical Perspective: Tools For Information to Flow Securely and Swift-ly
Building Secure Web Applications With Automatic Partitioning
Technical Perspective: The Complexity of Computing Nash Equilibrium
The Complexity of Computing a Nash Equilibrium
Networks of Contextualized Data: a Framework For Cyberinfrastructure Data Management
For Sale By Owner Online: Who Gets the Saved Commission?
Oracle, Where Shall I Submit My Papers?
Automatically Profiling the Author of an Anonymous Text
Shadow Systems: the Good, the Bad and the Ugly
Why Is Management Is In Trouble and How to Save It: Lessons Learned in the Automotive Industry
Why File Sharing Networks Are Dangerous?
Technical Opinion: Multitasking With Laptops During Meetings
wisePad Services For Vision-, Hearing-, and Speech-Impaired Users
Computational Challenges in E-Commerce
Technical Perspective: Customizing Media to Displays
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get InvolvedCommunications of the ACM (CACM) is now a fully Open Access publication.
By opening CACM to the world, we hope to increase engagement among the broader computer science community and encourage non-members to discover the rich resources ACM has to offer.
Learn More