Unsupervised Learning of Hierarchical Representations with Convolutional Deep Belief Networks
Research and Advances
Understanding Sources of Ineffciency in General-Purpose Chips
Protecting Users of the Cyber Commons
Satisfiability Modulo Theories: Introduction and Applications
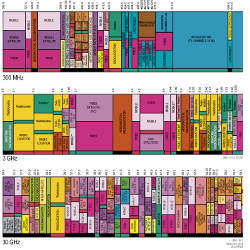
Realizing the Future of Wireless Data Communications
Vetting Browser Extensions For Security Vulnerabilities with VEX
Abstracting Abstract Machines: A Systematic Approach to Higher-Order Program Analysis
Technical Perspective: Making Browser Extensions Secure
Technical Perspective: Abstracting Abstract Machines
Calculating and Improving ROI in Software and System Programs
Quantitative Analysis of Real-Time Systems Using Priced Timed Automata
Crossing to the Dark Side: Examining Creators, Outcomes, and Inhibitors of Technostress
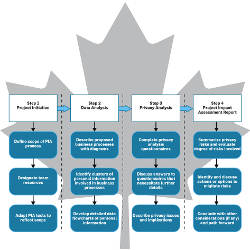
Should Privacy Impact Assessments Be Mandatory?
Theory and Applications of b-Bit Minwise Hashing
Cyberwarfare: Connecting the Dots in Cyber Intelligence
Reputation Systems For Open Collaboration
Gender and Computing Conference Papers
Technical Perspective: Sketches Get Sketchier
Technical Perspective: Skintroducing the Future
Skinput: Appropriating the Skin as an Interactive Canvas
An Overview of Business Intelligence Technology
Debugging in the (Very) Large: Ten Years of Implementation and Experience
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get InvolvedCommunications of the ACM (CACM) is now a fully Open Access publication.
By opening CACM to the world, we hope to increase engagement among the broader computer science community and encourage non-members to discover the rich resources ACM has to offer.
Learn More