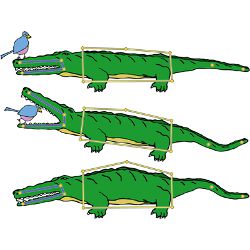
Motion Fields For Interactive Character Locomotion
Research and Advances
The Community Source Approach to Software Development and the Kuali Experience
Reducing the Software Value Gap
Cloud Security: A Gathering Storm
Understanding the Empirical Hardness of NP-Complete Problems
Technical Perspective: The Interplay of Neuroscience and Cryptography
Neuroscience Meets Cryptography: Crypto Primitives Secure Against Rubber Hose Attacks
Unifying Functional and Object-Oriented Programming with Scala
Who Does What in a Massive Open Online Course?
Security and Privacy For Augmented Reality Systems
Bounded Biharmonic Weights For Real-Time Deformation
Technical Perspective: A ‘Reasonable’ Solution to Deformation Methods
Making Parallel Programs Reliable with Stable Multithreading
Big-Data Applications in the Government Sector
In the same way businesses use big data to pursue profits, governments use it to promote the public good.
Using Targeted Conferences to Recruit Women Into Computer Science
TaintDroid: An Information Flow Tracking System For Real-Time Privacy Monitoring on Smartphones
Technical Perspective: Smartphone Security ‘Taint’ What It Used to Be
Communication Costs of Strassen’s Matrix Multiplication
Cryptography Miracles, Secure Auctions, Matching Problem Verification
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get InvolvedCommunications of the ACM (CACM) is now a fully Open Access publication.
By opening CACM to the world, we hope to increase engagement among the broader computer science community and encourage non-members to discover the rich resources ACM has to offer.
Learn More