It Is a Pivotal Time For K-12 Computer Science
December 2009 - Vol. 52 No. 12

Features
In CS Education, Educate the Educators First
CS Woes: Deadline-Driven Research, Academic Inequality
Crowdsourcing and the Question of Expertise
Israel’s Technology Industry as an Economic Growth Engine
A ‘Smart’ Cyberinfrastructure For Research
A Threat Analysis of RFID Passports
Maximizing Power Efficiency with Asymmetric Multicore Systems
The Bulk Multicore Architecture For Improved Programmability
Computer Science in the Conceptual Age
Computer Games and Traditional CS Courses
Technical Perspective: Design Tools For the Rest of Us
Designing Plush Toys With a Computer
Technical Perspective: A Graphical Sense of Touch
ThinSight: A Thin Form-Factor Interactive Surface Technology
Puzzled: Solutions and Sources
Power and Trust in Global Virtual Teams
Online Privacy, Government Surveillance and National ID Cards
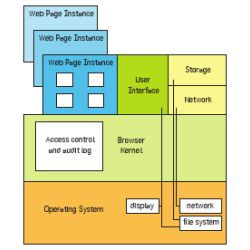
Security in Dynamic Web Content Management Systems Applications
Assessing Open Source Software as a Scholarly Contribution
Visual Passwords: Cure-All or Snake-Oil?
Positive Externality, Increasing Returns, and the Rise in Cybercrimes
Are Employees Putting Your Company At Risk By Not Following Information Security Policies?