Security and Privacy
Validating Factual Personal Information
Unlocking the Potential of Zero-Knowledge Proofs in Blockchain
Protecting Life-Saving Medical Devices From Cyberattack
Creating the First Confidential GPUs
Hardware VM Isolation in the Cloud
Confidential Computing: Elevating Cloud Security and Privacy
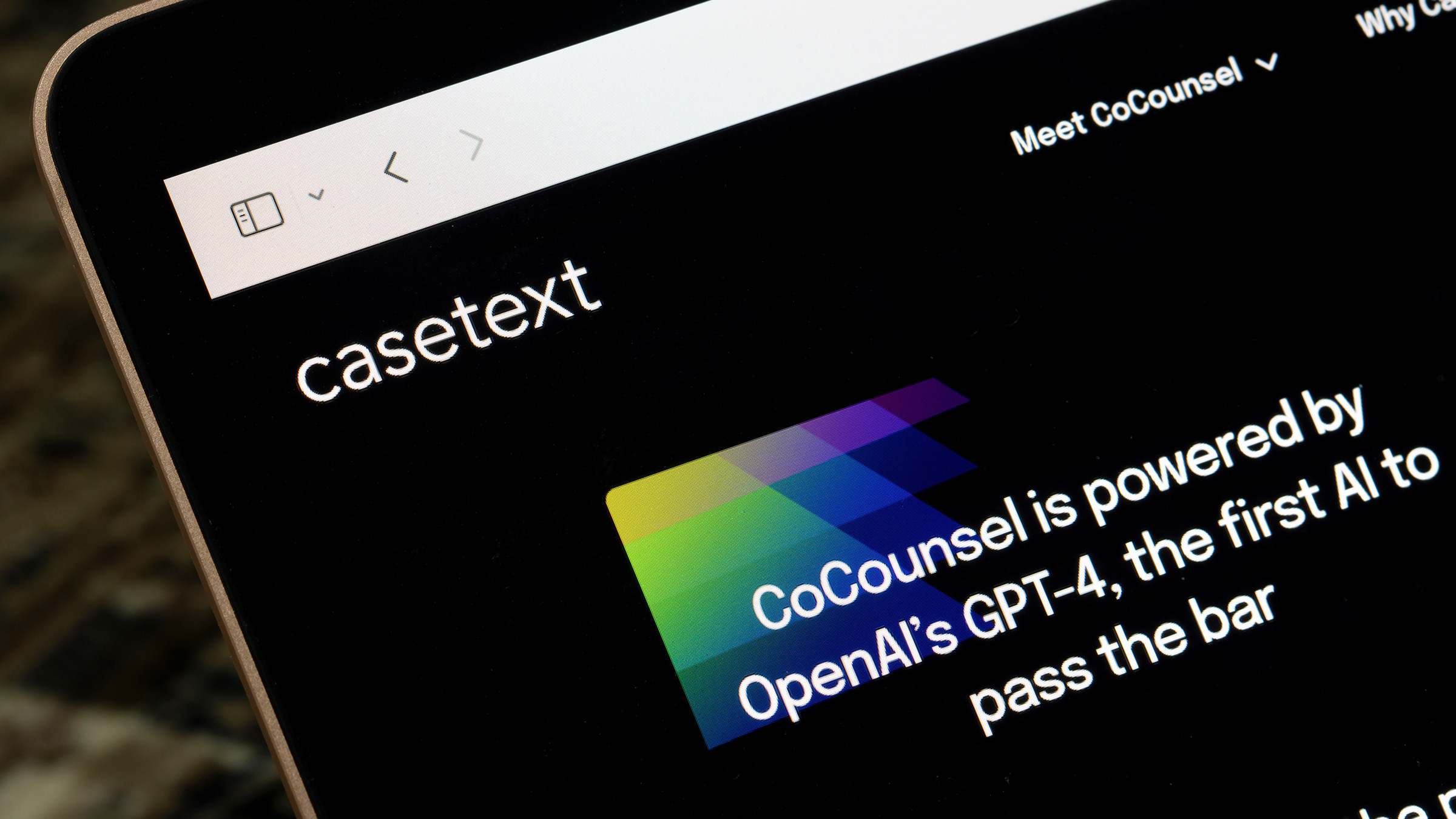
Generative artificial intelligence and the law: there is no turning back.
Multiple Data Leaks at 23andme
Magnetic Sensors Pinpoint GPU Cryptojacking Attacks
All Photos are Fake Until Proven Real
Should Schools Rely on Government for Cyber Protection?
Technical Perspective: A Rare Glimpse of Tracking Fake Reviews
"Leveraging Social Media to Buy Fake Reviews," by Sherry He et al., represents a breakthrough in our empirical understanding of fake reviews on Amazon.
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get InvolvedCommunications of the ACM (CACM) is now a fully Open Access publication.
By opening CACM to the world, we hope to increase engagement among the broader computer science community and encourage non-members to discover the rich resources ACM has to offer.
Learn More