Seam Carving For Media Retargeting
Research and Advances
Technical Perspective: Finding and Telling Stories with Data
Voyagers and Voyeurs: Supporting Asynchronous Collaborative Visualization
Automating Commonsense Reasoning Using the Event Calculus
Active Citizen Participation Using ICT Tools
Understanding the Adopters and Non-Adopters of Broadband
Improved Security Through Information Security Governance
Exploring the Black Box of Task-Technology Fit
Disaster Response in Health Care: A Design Extension For Enterprise Data Warehouse
The Relationship Between Software Development Team Size and Software Development Cost
Why Ebay Lost to Taobao in China: The Glocal Advantage
Open Information Extraction from the Web
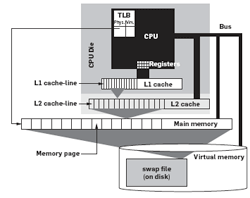
Breaking the Memory Wall in MonetDB
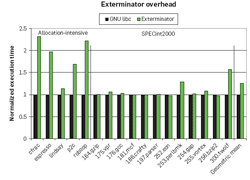
Exterminator: Automatically Correcting Memory Errors with High Probability
Got Data? A Guide to Data Preservation in the Information Age
Ontologies and the Semantic Web
Technical Perspective: One Size Fits All: An Idea Whose Time Has Come and Gone
Technical Perspective: Patching Program Errors
Enhancing Business Performance via Vendor Managed Inventory Applications
A Framework of ICT Exploitation For E-Participation Initiatives
Evolving Innovations Through Design and Use
Two Approaches to an Information Security Laboratory
Opening Up to Agile Games Development
Worst Practices in Search Engine Optimization
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get InvolvedCommunications of the ACM (CACM) is now a fully Open Access publication.
By opening CACM to the world, we hope to increase engagement among the broader computer science community and encourage non-members to discover the rich resources ACM has to offer.
Learn More