Privacy-Preserving Network Forensics
Research and Advances
Brain-Computer Interfaces For Communication and Control
Computational Complexity and Information Asymmetry in Financial Products
Technical Perspective: Images Everywhere Looking For Models
Technical Perspective: Complex Financial Products: <i>Caveat Emptor</i>
Self-Similarity-Based Image Denoising
Crowdsourcing Systems on the World-Wide Web
Technical Perspective: Patterns Hidden from Simple Algorithms
Poly-Logarithmic Independence Fools Bounded-Depth Boolean Circuits
Technical Perspective: Liability Issues in Software Engineering
Liability Issues in Software Engineering: The Use of Formal Methods to Reduce Legal Uncertainties
Achievements and Challenges in Software Reverse Engineering
Emergency! Web 2.0 to the Rescue!
A Research Doctorate For Computing Professionals
Why STM Can Be More Than A Research Toy
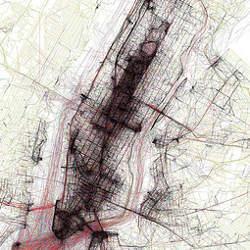
Design Principles For Visual Communication
Reflecting on the DARPA Red Balloon Challenge
Data Structures in the Multicore Age
Understanding Scam Victims: Seven Principles For Systems Security
Technical Perspective: Concerto For Violin and Markov Model
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get InvolvedCommunications of the ACM (CACM) is now a fully Open Access publication.
By opening CACM to the world, we hope to increase engagement among the broader computer science community and encourage non-members to discover the rich resources ACM has to offer.
Learn More