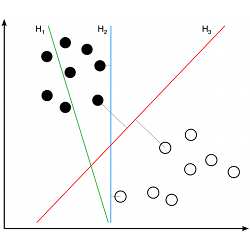
Computational Learning Techniques Becoming Mainstream
What Can Be Done About Gender Diversity in Computing?: A Lot!
Why Doesn’t ACM Have a SIG For Theoretical Computer Science?
Wireless Sensor Networks and the Risks of Vigilance
Why Security Standards Sometimes Fail
Spanning the Chasm of the K–12 and Post-Secondary Relationship
Why HCI Should Listen to Mothers
Closing the Computing Labor Shortage with Computing in Schools
Ma Bell’s Revenge: The Battle For Network Neutrality
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get InvolvedCommunications of the ACM (CACM) is now a fully Open Access publication.
By opening CACM to the world, we hope to increase engagement among the broader computer science community and encourage non-members to discover the rich resources ACM has to offer.
Learn More