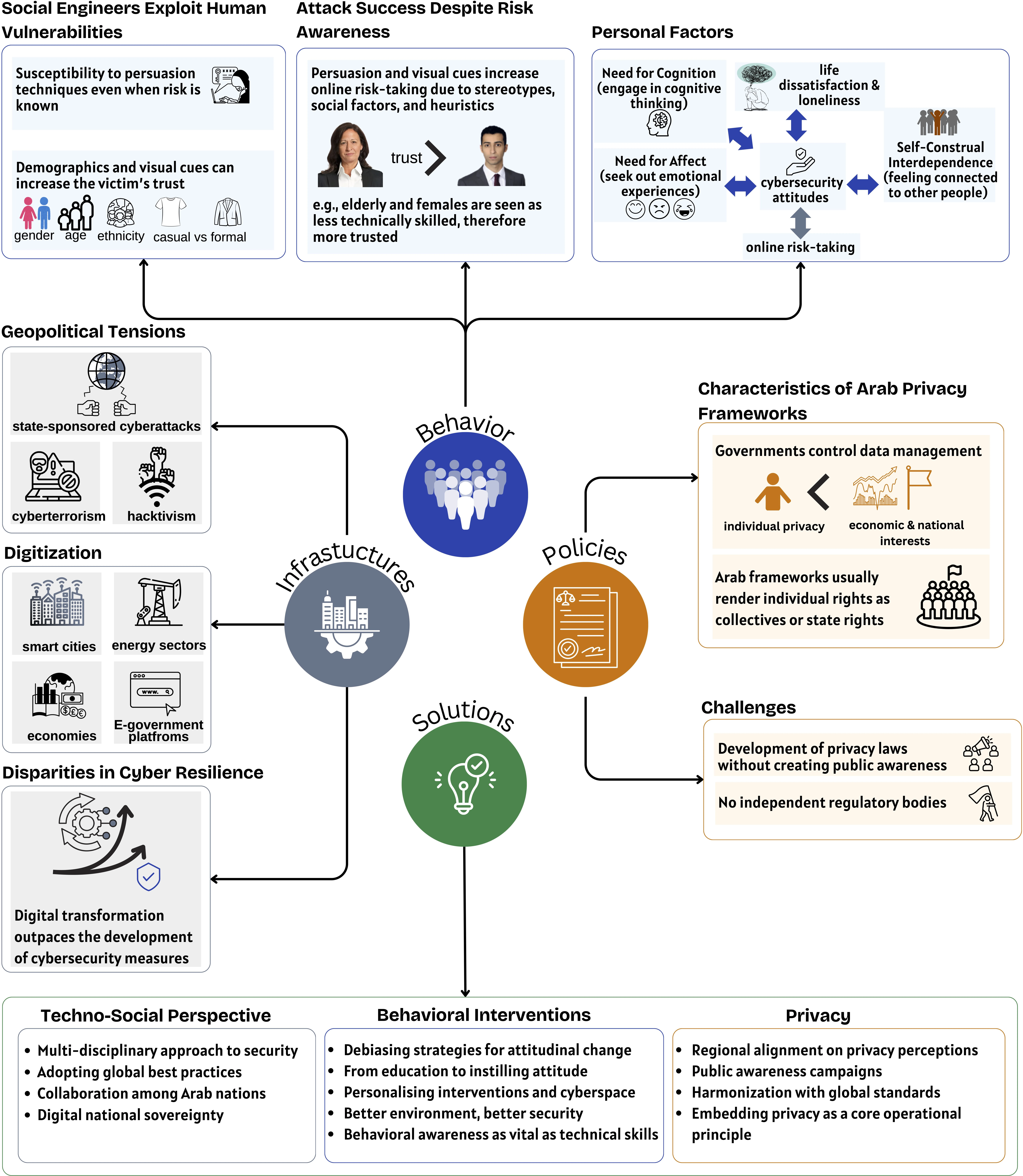
Interconnected systems have become the backbone of modern societies. However, the very same critical role played by these systems brings significant challenges: Securing interconnected systems is not merely a technological necessity, but a cornerstone for safeguarding the economic, political, and social stability of countries.16 While these challenges are global, the Arab World presents a unique landscape that warrants a nuanced exploration of both commonalities and peculiarities within the broader context of securing interconnected systems (see Figure for a brief summary of these challenges).
Common Challenges in Securing Interconnected Systems
Interconnected systems, including cyber-physical systems, often combine computational and physical processes. They include critical infrastructure such as power grids, transportation networks, and healthcare systems, alongside commercial and industrial applications.10 The secure operation of these systems hinges on several factors: resilience against cyberattacks, data integrity, user authentication, and the ability to detect and mitigate threats in real time. One of the primary challenges is the increasing sophistication of cyber threats. Advanced persistent threats exploit vulnerabilities in software, hardware, and human operators, often leveraging zero-day exploits and social engineering tactics. The global nature of supply chains further complicates security, as compromised components can introduce vulnerabilities at scale.19 Furthermore, the Internet of Things revolution has exponentially increased the number of connected devices, expanding the attack surface and necessitating scalable and robust security measures.
Securing Interconnected Systems in the Arab World: Idiosyncratic Challenges
The Arab World shares many of the above-mentioned global challenges, but it also presents distinctive characteristics that influence the security of interconnected systems. For instance, the region is experiencing an ever-increasing investment in smart cities, e-governance platforms, and digital economies, resulting in a faster adoption and penetration of these technologies than the Western World. However, the geopolitical landscape of the Arab World also introduces unique vulnerabilities. The region historically has been a focal point for geopolitical tensions, which often extend into the cyber domain. State-sponsored cyberattacks, hacktivism, and cyberterrorism are prevalent, targeting critical infrastructure such as oil and gas facilities, financial institutions, and government networks.18
Another peculiarity is the reliance on oil and gas as economic pillars. The digitization of the energy sector, while improving efficiency, also exposes it to cyber threats. For instance, a cyberattack on a major oil refinery or pipeline can have cascading effects, not only on the national economy but also on global energy markets.16 Climate also plays a distinguished role. The harsh conditions (desertic/semi-desertic) of many of the Arab countries make the reliance on dams and desalinization facilities a critical aspect of sustaining even daily life; the security of such infrastructures has a direct impact on the safety of hundreds of millions of people living in the region—paradoxically, desalinization facilities in some of the Gulf Cooperation Council (GCC) countries, characterized by the absence of stable rivers or lakes, are more critical assets than oil fields.
Moreover, the region’s rapid digital transformation often outpaces the development of cybersecurity measures. While some GCC countries have made significant strides in implementing national cybersecurity strategies, and others are close followers, creating a certain degree of disparity in the region’s overall cyber resilience.18 Also, demographics play a major role: with more than 60% of the population being below their thirties, a large part of Internet access is realized through mobile, this latter point bringing in its own security issues.20 Finally, cultural and linguistic factors influence cybersecurity as well. For instance, the limited availability of cybersecurity tools and training in Arabic creates barriers to building a robust cybersecurity workforce.
Security as a Behavior
Human attitudes and behaviors, including those related to security and risk-taking, are shaped by various factors and differ across cultures due to distinct norms. Arab cultures (as a regional cluster), for instance, emphasize collectivism and high power-distance, promoting group cohesion and respect for authority.23 These traits may encourage compliance with security guidelines but may also leave individuals vulnerable to manipulation based on what may appear socially validated and authorized. In contrast, Western cultures tend to prioritize individualism, encouraging users to make independent judgments about online content, even when endorsed by others. This same independence may also give scammers a chance to succeed, despite legitimate public skepticism about the questionable nature of their messages.
How persuasion and appearance impact security behavior. Recent research has examined the role of influence in social engineering and cybersecurity. As humans often are considered the weakest link in security systems, protecting them from persuasive attempts and negligent behavior is as critical as technical defenses. Cialdini’s principles of influence provide a well-known framework for categorizing mechanisms of persuasion: scarcity, reciprocity, social proof, likability, commitment and consistency, and authority.6 Additionally, demographic and appearance cues often serve as cognitive shortcuts for determining trustworthiness, which manipulators can exploit by adopting trust-inspiring personas. Recent research has examined these two aspects as examples of human factors in cybersecurity within Arab countries, specifically the GCC region and the United Kingdom (U.K.), as a benchmark for comparison.
In Mollazehi et al.13 it was shown that, in both the U.K. and the Arab samples, scenarios applying Cialdini’s principles of influence were more effective in instilling trust and willingness to take online risks compared to their counterpart scenarios, i.e., neutral versions without influence principles. Participants had to recognize at least minimal risk in the online scenarios to ensure their responses accurately represent risk-taking. These principles increase risk-taking due to factors related to stereotypical perceptions, decision-making processes, and social influences.14
Demographics and visual appearance were further explored using 16 scenarios,2 representing combinations of age (older vs. younger), gender (male vs. female), ethnic similarity (Arab vs. U.K.), and clothing (formal vs. casual). Arab participants placed more trust and showed greater willingness to take security risks with individuals who were female, older, Arab, or formally dressed compared to their counterparts who were male, younger, British, or casually dressed (see Figure). British participants exhibited similar trends, except that ethnic similarity had no significant impact. Some additional cultural differences were observed in the willingness to trust older people. Arab participants had higher trust in middle-aged men and women than in young men and women. However, in the U.K. context, this pattern was observed only for women, with no conclusive evidence for men. When investigating the reasons behind these findings,1 it was discovered that these biases stemmed from stereotypical perceptions related to technical skills, social expectations, affinity effects, and other factors. The qualitative study revealed that participants often justified their decisions with reasoning such as “most hackers are young men.” This type of reasoning can be anticipated and exploited by manipulators, for instance, by recruiting middle-aged women for social engineering attacks.
The influence of individual differences. Personal factors also affect attitudes toward implementing cybersecurity recommendations. For instance, people who were less satisfied with their lives and felt lonelier were more likely to develop Internet addiction, which was linked to a lower intention to follow good cybersecurity practices.7 A study of U.K. and Arab samples found that the need for affect (seeking emotional experiences) and the need for cognition (enjoying problem-solving) positively predicted Security Attitudes (SAs) in both groups.3 Surprisingly, individuals with high SA in both Arab and U.K. samples showed a greater tendency for risk-taking when influenced by certain persuasion principles.15
This suggests that high SA may lead to increased risk-taking due to a false sense of control, regardless of cultural background. The same study also revealed cultural differences: only Arab participants showed increased risk-taking when approached by someone recognized as an expert. Other personal factors, such as interdependent self-construal (viewing oneself as connected to others, prioritizing group harmony and social roles), had a positive impact on SA among Arab individuals only, whereas independent self-construal (seeing oneself as a distinct individual, emphasizing personal goals, autonomy, and self-expression) had an impact in both cultural contexts.21
In summary, humans tend to behave similarly in security contexts, though nuances arising from personal and cultural differences still exist. This means countermeasures should also be tailored, for example, by increasing awareness of homophily and the similarity-attraction effect, particularly among Arabs, where ethnic similarity has been shown to significantly enhance trust in strangers.2
Evolving Privacy Cultures and Legal Orientations in the Arab World
As digital infrastructures expand across the Arab World, privacy governance is emerging not only for legal requirements, but as a reflection of broader cultural, institutional, and developmental dynamics. The region’s evolving frameworks are shaped by distinct understandings of privacy, rooted in norms around social trust, the role of the state, and collective responsibility. These cultural orientations do not oppose global standards but intersect with them, resulting in a unique pattern of legal adaptation and institutional design.
Recent regulatory reforms, ranging from newly enacted data protection laws to regional initiatives, highlight the growing institutionalization of privacy. However, these frameworks are not culturally neutral. Many Arab legal systems are grounded in traditions that emphasize communal values and public interest, shaping how privacy is conceptualized and operationalized.17,22 This cultural lens often informs decisions around data ownership, permissible data use, and the balance between individual rights and societal needs.
Institutionally, privacy regulation often reflects centralized governance models. Oversight typically is entrusted to government bodies, aligning with prevailing administrative structures.8,22 While this design supports integration with national policy priorities, it also raises important questions around regulatory autonomy and long-term enforcement capacity. It contrasts with approaches like the European Union’s, which emphasize independent supervisory authorities, but it shares parallels with other globally recognized frameworks such as China’s Personal Information Protection Law (PIPL) or the early stages of Japan’s Act on the Protection of Personal Information (APPI).
Regarding legal content, Arab privacy laws incorporate globally recognized rights, including access, correction, erasure, and consent.8,11 However, the implementation of some rights, such as data portability or objection to automated profiling, varies depending on institutional maturity and public awareness. Many frameworks remain in early enforcement phases focused on capacity building, professional training, and compliance readiness. When compared with international standards, Arab privacy exhibits functional convergence with instruments like the GDPR, PIPL, APPI, the California Privacy Protection Agency, and the California Consumer Privacy Act17 through pathways that align with regional governance logics. Enforcement is often cautious but evolving. Regulatory scope is broad, sometimes including extraterritorial applicability and significant penalties. Data localization requirements, designed to ensure domestic oversight of sensitive information, feature prominently in many Arab laws, distinguishing them from more liberal data transfer regimes.
The interplay between regional cultural contexts and global normative frameworks is evident in how privacy is framed within the national discourse. In many Arab societies, privacy is not solely a legal entitlement, but also a social expectation mediated by family, faith, and institutional trust. Legal frameworks do not evolve in a vacuum, but alongside public attitudes forming around digital rights and obligations.
Regional cooperation, such as the Arab Convention on Personal Data Protection and model laws developed by the Economic and Social Commission for Western Asia, suggests a shared interest in enhancing legal interoperability.9 These efforts support the gradual emergence of a regional privacy culture: one that respects global norms while reflecting localized perspectives on governance, accountability, and the social contract. In conclusion, privacy governance in the Arab World is neither static nor derivative. It is a dynamic process of negotiation between legal harmonization and cultural relevance, between external benchmarks and internal values. Understanding this evolving landscape requires considering the laws themselves within cultural narratives, institutional choices, and regional aspirations that animate them.
The Way Forward
In this section, we recap the different dimensions discussed above and provide a unified view about the issues, challenges, and possible remedies, also synthesized in the Figure.
Techno-social perspective. Securing interconnected systems in the Arab World requires a multidisciplinary, culturally informed approach that integrates technological advancement with sociopolitical realities. While global best practices provide a useful foundation, region-specific challenges must be addressed through coordinated national efforts and interstate cooperation. Two pressing and closely linked priorities are, first, investing in national computing infrastructure—such as datacenters—to support digital growth, and second, developing a clear, forward-looking approach to Artificial Intelligence (AI), including policies for ethical use, talent development, and alignment with national goals. Satisfying the need for computational resources via outsourcing to foreign entities poses risks related to data confidentiality, sovereignty (especially in politically fluid environments), and cost. A cooperative regional approach could mitigate these risks by leveraging the Arab World’s geographic and economic advantages (for instance, low energy costs) to develop shared datacenters and computing facilities. This would not only strengthen digital autonomy but also foster a skilled local workforce. Concurrently, addressing the AI race entails more than computing infrastructures; it requires widespread digital literacy and AI education, with security and trust being necessary components. Security awareness campaigns and training programs, tailored to local languages and cultural norms, are essential to instill secure practices and build societal resilience. Public trust can be enhanced by aligning cybersecurity frameworks with traditional governance structures and using familiar communication channels, such as community forums. Ultimately, the region’s trajectory depends on how it addresses these challenges. Fragmented efforts risk deepening intra-regional divides, while a cooperative strategy could unlock significant technological and intellectual potential, positioning the Arab World as an influential contributor to global cybersecurity and AI development.
Behavioral interventions. Security behavior is complex and influenced by both personal and situational factors, where a mere explanation of what is right and wrong is not sufficient. Some of the biases that make people susceptible to manipulation are deeply ingrained. First, we recommend using immersive methods such as rehearsal and simulation, with the aim of more effectively instilling secure attitudes than through traditional literacy delivery alone. Second, we suggest equipping individuals with psychological literacy, including awareness of debiasing strategies, manipulation techniques, and the influence of personal and cultural traits on decision-making.2,13,15 The third recommendation highlights the need to tailor training programs and digital environments to individual differences, acknowledging the moderating role of culture in how these differences affect security behavior. For example, for individuals with a low need for cognition within Arab cultural contexts, literacy programs should adopt a more motivational approach.3 Fourth, we advise improving the environments in which people live and work, as feelings of connection and job security may support healthier cyber behavior.7 Moreover, bridging digital divides ensures equitable access to secure technologies, reducing systemic vulnerabilities. Regional collaboration among Arab nations can amplify collective resilience, while international partnerships foster knowledge exchange and innovation. By weaving together infrastructure, behavioral insights, and culturally attuned policies, the Arab World can build not only secure systems but also a foundation for a sustainable and inclusive digital future. Privacy is shaped by social norms as much as by law. Behavioral strategies must reflect this, designing interventions that account for local trust dynamics and cultural perceptions.
Privacy. Privacy behavior is shaped by legal awareness, cultural expectations, and institutional capacity. In this context, several key actions are proposed. First, investing in capacity building is essential—training data protection officers and legal professionals to interpret and apply privacy laws effectively. Second, public awareness should be raised through sustained campaigns, drawing inspiration from initiatives like Bahrain’s, to foster a shared understanding of data protection. Third, aligning with global standards is critical, particularly by adapting GDPR principles to local contexts while preserving individual rights. Allowing transitional periods will help businesses comply progressively. Fourth, privacy should be promoted by design and by default, embedding privacy-preserving features directly into systems and workflows to ensure privacy is integral rather than optional. Fifth, regional cooperation mechanisms—such as shared frameworks or model laws—can reduce legal fragmentation while honoring cultural differences. Lastly, AI should be leveraged to support privacy objectives by automating compliance, enhancing data anonymization, detecting threats, and offering personalized privacy controls. For these reforms to be effective, public understanding must evolve in tandem with regulation. Legal literacy needs to become part of daily behavior, reinforced by cultural relevance, institutional readiness, and continuous engagement with both global standards and local realities.
Acknowledgments
We would like to thank the anonymous reviewers for their help in improving the presentation and clarity of the contribution.
This publication was partly supported by NPRP 14 Cluster grant number NPRP 14C-0916–210015 from the Qatar National Research Fund (a member of Qatar Foundation). The findings herein reflect the work and are solely the responsibility of the authors.



Join the Discussion (0)
Become a Member or Sign In to Post a Comment