Abstract
Despite being a quintessential example of a hard problem, the quest for finding fast algorithms for deciding satisfiability of propositional formulas has occupied computer scientists both in theory and in practice. In this article, we survey recent progress on designing algorithms with strong refutation guarantees for smoothed instances of the k-SAT problem. Smoothed instances are formed by slight random perturbations of arbitrary instances, and their study is a way to bridge the gap between worst-case and average-case models of problem instances. Our methods yield new algorithms for smoothed k-SAT instances with guarantees that match those for the significantly simpler and well-studied model of random formulas. Additionally, they have led to a novel and unexpected line of attack on some longstanding extremal combinatorial problems in graph theory and coding theory. As an example, we will discuss the resolution of a 2008 conjecture of Feige on the existence of short cycles in hypergraphs.
1. Introduction
The famous SAT problem asks to determine if a given propositional formula is satisfiable. That is, can we set the formula’s variables to 0 (False) or 1 (True) in a way so that the formula evaluates to 1 (True). In this article, we will focus on the -SAT problem where the propositional formula is further restricted to be in the -CNF form, that is, logical AND of a collection of -clauses, each of which is a logical OR of at most literals (variables or their logical negations). For example, is a 3-CNF formula in variables where , and denote the logical AND, OR and NOT operations, respectively. Given a -CNF formula, we are interested in either finding a satisfying truth assignment, if it exists, or a “refutation”—a short, easily-checkable proof that the formula is unsatisfiable. Despite its simplicity, -SAT is phenomenally expressive and models a long list of important discrete optimization problems. A decades-long quest has thus focused on designing algorithms for -SAT in both theory and practice.
In this article, we will focus on finding refutations—“obviously verifiable” polynomial size (that is, short) contradictions that confirm unsatisfiability of a -SAT formula. For any formula, we can simply a tabulate each of the possible truth assignments together with a clause violated by . This is an obviously verifiable refutation but clearly too long—it’s exponential in size. On the other hand, if we get lucky and our formula happens to contain two 1-clauses , then it is manifestly unsatisfiable and the two 1-clauses serve as an easily verifiable and short certificate of unsatisfiability. Of course, it’s unrealistic for such clauses to magically occur in interesting inputs. But we can often infer additional clauses that must also be satisfied if the input formula is satisfied and hope that such an obviously verifiable short contradiction arises in the inferred clauses. Such clause learning (via mechanical resolution rules) for deriving new clauses form an integral part of practical SAT solvers.
In his famous 1972 paper,18 Karp proved that ascertaining satisfiability or finding refutations for 3-SAT formulas is NP-hard. Thus, finding a fast algorithm for 3-SAT that succeeds (even approximately) on all possible input is likely hard. One might naturally expect finding refutations to get easier as the number of clauses increases (more clauses means more possibilities for contradictions to manifest), and so perhaps one might hope that denser instances get easier? No such luck! As it turns out, unless a widely believed, stronger variant of the conjecture fails, there are no polynomial time algorithms for refuting -SAT formulas unless they have essentially the maximum possible (out of possible) clauses. In fact, even substantially beating brute-force search and finding sub-exponential (for example, ) time algorithms is ruled out for formulas with clauses.14
Despite the grim picture presented by these hardness results, the extraordinary modeling power of -SAT has motivated a concerted research effort for finding fast heuristics for -SAT. On the practical side, new algorithmic ideas along with advances in software engineering have made modern SAT solvers13 a powerful and indispensable tool with applications to solving practical instances of optimization problems in planning, model checking, and verification of software systems. By encoding the task of finding counter-examples to mathematical conjectures into SAT formulas, SAT solvers have even helped resolve longstanding mathematical conjectures.6 On the theoretical side, algorithms research has focused on more careful modeling of input instances to escape worst-case hardness under minimal assumptions. Such beyond worst-case input models for hard discrete optimization problems such as -SAT now form a vibrant area11 of research in algorithm design.
1.1 The Smoothed -SAT Model
In 2007, Feige proposed9 his smoothed -SAT model as a way to circumvent the all-pervasive hardness of -SAT. He was inspired by a groundbreaking work of Spielman and Teng on smoothed analysis of the simplex algorithm. The simplex algorithm for linear programming, introduced by Dantzig in 1947, presented an uncomfortable disconnect between theoretical predictions and practical performance—here was a fast practical algorithm that also provably needed exponential time in the worst-case! In 2001, Spielman and Teng convincingly resolved23 this tension and showed that the simplex method runs in polynomial time on smoothed inputs—an input obtained by adding a small random perturbation to an arbitrary instance. Such a perturbation, of the sort one might reasonably expect practical instances to naturally possess, is enough to remove all hardness in even carefully crafted instances.
Feige’s model involves an analogous smoothening of a worst case -SAT formula by randomly perturbing each literal (that is, changing an unnegated variable to negated and vice-versa) in each clause with some small probability, say , independently. For example, given two clauses , we imagine tossing 6 independent coins with bias , one for each literal in each of the two clauses. The smoothed version of the first clause, will have, for example, negated if the first coin lands on heads, unnegated if the 2nd coin lands on heads, and so on.
If the input formula has clauses in variables for some large enough constant , then the resulting smoothed formula is unsatisfiable with high probability over the random perturbation. Feige thus asked if the task of finding refutations for smoothed -SAT formulas gets significantly easier when compared to worst-case formulas. Equivalently, given our discussion above, do clause-smoothed -SAT formulas admit efficient refutation algorithms?
Prior works2,8,22 showed that the answer is indeed yes for the random -SAT model—a fully smoothed model where the negation patterns and the clause structure, that is, the variables appearing in the clauses (that are worst-case in smoothed -SAT) are chosen independently at random. However, those algorithms strongly exploit the abundant randomness in the choice of variables appearing in the clauses.
In this article, we will survey recent developments1,16,17 on a new class of algorithms, based on the eigenvalues of certain specialized Kikuchi matrices (introduced earlier24 for statistical inference and to simplify algorithms for random -SAT22 for even ), that yield optimal (modulo certain hardness conjectures) algorithms for smoothed -SAT. As a result, these new algorithms succeed in refuting smoothed -SAT formulas with clauses, that is, , in polynomial time and significantly beat brute-force search if . In fact, our guarantees for smoothed -SAT match the best-known (and conjectured optimal) results for the significantly simpler and restricted setting of random-SAT formulas, provide quantitative bounds on the number of clauses that every truth assignment must violate, and extend far beyond -SAT to handle all logical constraint satisfaction problems.
1.2 Spectral Methods for Combinatorics
While the theoretical advances in algorithms for -SAT haven’t yet influenced practical SAT-solving, they already have some surprising applications to long open problems in other areas of mathematics. These include resolving Feige’s conjecture on small even covers (cycles) in hypergraphs,16,17 making progress on the decades-long quest for optimal bounds for locally decodable4 and locally correctable19 error-correcting codes, and problems7 in additive number theory that generalize the famous Szemeredi’s theorem.
The principle behind such applications is analogous to how SAT solvers helped resolve mathematical conjectures by encoding the search for a proof into a SAT formula. Our theoretical analog strongly exploits the newfound ability to tackle -SAT formulas with a worst-case clause structure. In this article, we will discuss an application of this method to proving Feige’s conjecture on small cycles in hypergraphs. Surprisingly, proving this conjecture will let us go full circle to show even better refutations for smoothed -SAT.
Short Cycles in Graphs.
Feige’s conjecture10 is a generalization of a basic result about short cycles in graphs. Recall that a graph (aka network), is simply a collection of pairs, called edges (modeling pairwise associations), on nodes. A cycle in such a network is a sequence of nodes that starts and ends at the same node such that every consecutive pair has an edge between them. In his famous 1978 book,5 mathematician Béla Bollobás conjectured that every graph with nodes where every node, on average, has edges (this quantity is called the average degree), must have a cycle of length at most . When , the network can be a single giant cycle on all vertices that clearly has no cycle of length . For any , however, the conjecture implies that we cannot even avoid a cycle of length —an exponentially smaller bound than —and thus signals a phase transition in the extremal length of the smallest cycle as the average degree crosses 2.
Bollobas’s conjecture is an example of a result in extremal combinatorics. Such results uncover a truth that holds for all (thus extremal) mathematical objects. Here, it says that no matter how we might build a graph on nodes, so long as it has average degree , we cannot avoid introducing a short cycle. In their elegant 2002 paper,3 mathematicians Alon, Hoory and Linial confirmed this conjecture.
Short Cycles in Hypergraphs.
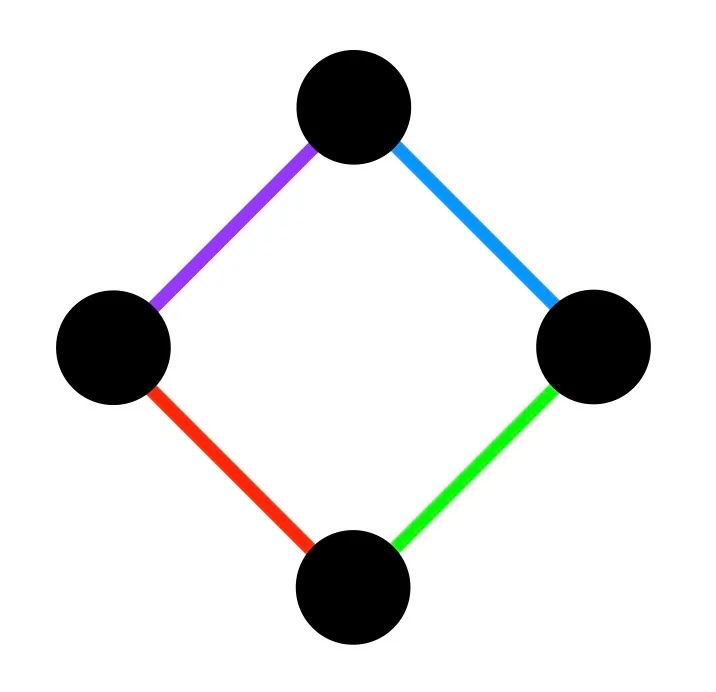
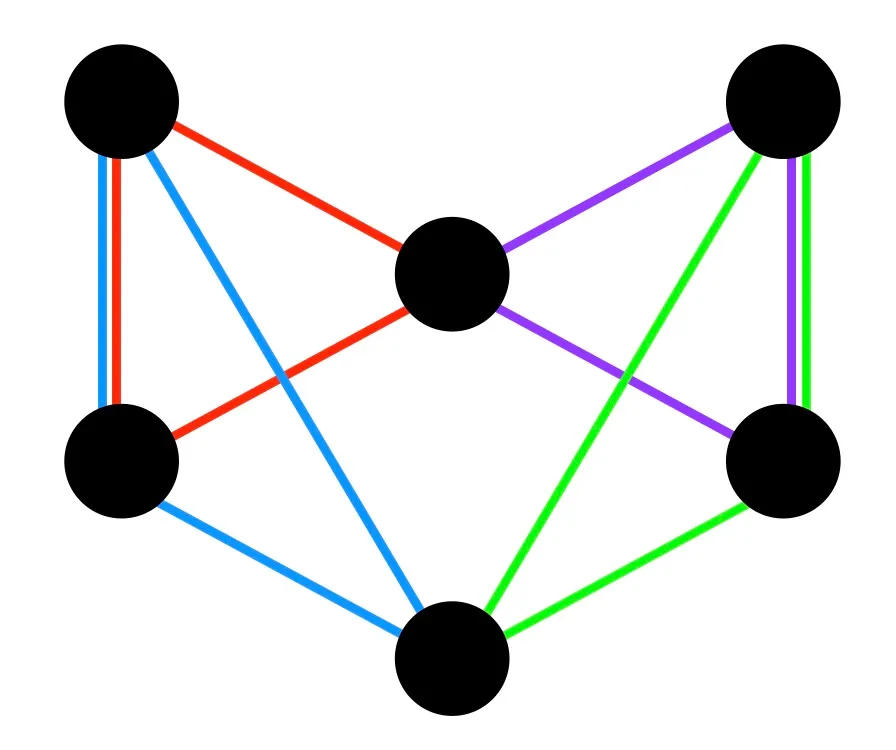
Feige’s conjecture asks a similar question about short cycles in hypergraphs. A -uniform hypergraph is a collection of subsets of size on nodes, called hyperedges, that model associations between a larger number of nodes (instead of 2 in graphs). A 2-uniform hypergraph is simply a graph. In order to pose Feige’s question, we will identify a key property of cycles in graphs and use it to motivate a generalized notion of cycles in hypergraphs. Observe that every vertex appears in either two or zero edges in any cycle in a graph. In particular, a cycle is an even subgraph—a subset of edges on which, every vertex appears an even integer number of times. Even subgraphs naturally generalize to hypergraphs. We will define a hypergraph cycle or even covers to be a collection of hyperedges such that every node of the hypergraph is included in an even number of ’s (that is, an even subhypergraph). (See Figure 1a and 1b.)
This definition may look odd (or perhaps a little too even?), at first. A cycle in a graph has an appealing combinatorial structure of a loop. Hypergraph cycles seem to lack a combinatorial meaning. Why did Feige (and why should we) care about it? Feige’s motivation for studying short cycles actually stemmed from to finding refutations for -SAT formulas (see next section). Here, we outline a different source of motivations that comes from deep connections to the theory of error correcting codes because hypergraph cycles naturally relate to solving systems of linear equations.
To see why, let’s associate a variable to every node of a graph and let’s think of each edge as specifying a linear equation modulo 2. Thus, the edge between nodes 1 and 2 relates to the equation mod 2 where . A cycle in the graph then naturally corresponds to a subset of 2-sparse (that is, each equation has only two non-zero coefficients) equations that is linearly dependent—that is, if you want this subset of equations to be satisfied, then the right hand side of at least one of the equations is already fixed (that is, cannot be chosen independently) once you fix the choice of the right hand sides for all the others. As a simple example, consider the graph on 3 nodes with edges , and . Suppose you knew that some satisfies the two equations corresponding to the first two edges mod 2 and is 1 mod 2. Then, adding the left hand sides of the two equations gives mod 2 which is equivalent to mod 2 since mod 2, regardless of the value of . Thus, the right hand side of third equation is determined/dependent and cannot be chosen independently of the first two equations. A cycle in a -uniform hypergraph similarly corresponds to a linearly dependent subset of -sparse (that is, each equation has non-zero coefficients) equations corresponding to each hyperedge.
The length of the smallest cycle thus equals the size of the smallest linearly dependent subset of equations in a given system. Understanding the size of such a set turns out to have a whole gamut of applications, especially in designing error-correcting codes. Error correcting codes (or just codes, in short) are a systematic method of adding redundancy to a message so that, when the message transmitted across a noisy channel and incurs errors, one can still decode it uniquely thanks to the redundancy. The systematic methods or codes naturally involve adding “parity checks”, that is, right hand sides of an appropriately chosen set of linear equations evaluated at the message. In such codes, the length of the smallest linearly dependent subset of equations naturally corresponds to distance—a crucial quantity that controls the number of errors that can be corrected. The smallest linear dependencies in -sparse equations turns out to be equivalent to understanding the best possible distance (and thus, the largest possible rate of errors that can be tolerated) by an important class of codes called low density parity check codes introduced by Gallager in 1960s with numerous theoretical and practical applications.
Feige’s Conjecture and the Resolution.
As in the case of graphs, we are interested in the extremal trade-off between average degree (that is, average number of hyperedges containing a node) and the length of the smallest hypergraph cycle in a -uniform hypergraph. Given the connection to linear dependencies above and the basic fact that every collection of equations in variables are linearly dependent, whenever the average degree , then the hypergraph must have a (rather long) cycle of length . Making an analogy to graphs, one might expect that if , the hypergraph must have a -length cycle, but this turns out to be false! Mathematicians Assaf Naor and Jacques Verstraete in 2006 showed21 that one needs (and this is enough!) the average degree in order for every hypergraph to have a -length cycle. For , this matches a coarse version of the bound for graphs but for suggests a new regime between and that has no analog for graphs. What happens when, for example, ? Feige conjectured a precise behavior for this regime:
Every -uniform hypergraph on nodes with average degree has an -length cycle.
Feige’s conjecture (up to some factors in ) was motivated by the hypothesis (and is, in fact, equivalent to it) that there is no better construction of hypergraphs avoiding short cycles than simply choosing a random hypergraph. It is thus analogous to the famous 1947 theorem of Shannon (the birthplace of modern coding theory!) that random error correcting codes are “best” in a precise sense.
Despite being a foundational statement about hypergraphs, the conjecture remained largely open with only some partial progress for a special case by Alon and Feige in 2009. Now, by invoking the new algorithms for solving smoothed -SAT we can essentially completely resolve it — up to one additional factor in the degree bound! This was established first by the authors with additional factors which were later17 trimmed down to a single factor.
Every -uniform hypergraph on nodes with average degree has an -length cycle.
As we will explain later in this article, the proof of this theorem makes a new connection between the success of our spectral approach for smoothed -SAT and existence of short cycles in hypergraphs. It forms the first (of a growing list of) application spectral refutations via Kikuchi matrices in combinatorics.
2. A New Spectral Approach
Our approach for finding refutations for smoothed -SAT formulas relies on continuous time algorithms based on spectral methods—methods that use eigenvalues and eigenvectors of matrices built from the input. This is in contrast to the largely discrete algorithmic toolkit (such as resolution refutations and their generalization) in modern practical SAT solvers. In fact, it has been known for more than 20 years that even random -SAT formulas with clauses do not admit efficient resolution refutations—a natural formalization of combinatorial refutations.
The spectral approach for refuting -SAT formulas was conceived15 by Goerdt and Krivilevich back in 2001. A decade and half of work led to spectral methods with conjectured-optimal guarantees for refuting random -SAT in 2017. These spectral methods, however, are rather brittle and strongly rely on the randomness in the variables appearing in each clause. For smoothed -SAT, such methods provably fail since the variables appearing in the clauses are completely arbitrary. In this article, we will present a new class of spectral methods, based on Kikuchi matrices, which, when combined with combinatorial pre-processing, provide robust methods for refutation that significantly simplify the results for random -SAT and extend to smoothed -SAT with no loss in performance.
From -SAT to Degree Polynomials.
To bring in spectral methods, we will make a simple but conceptually important translation between refuting a -SAT formula and finding certificates of upper bounds on the maximum value of a degree polynomial. For this purpose, it will be more convenient to view truth assignments as (True) and (False). Given a -SAT formula with clauses, let map truth assignments to the number of clauses satisfies by . Then, is clearly the sum of functions , one for each clause in where if and only if satisfies clause . Since depends only on -variables, it is a degree polynomial. For example, and :
(1)To refute the -SAT formula , we will find an easily-checkable certificate of the fact for all . In fact, we will certify a stronger bound of , that is, every must violate not just 1 but in fact of the clauses.
Observe that is a sum of 8 (in general, ) monomials, each of degree (, more generally). A standard idea, going back to early 2000s, is to certify bounds on 8 different polynomials, obtained by taking one out of 8 terms corresponding to each . We can then obtain a bound on by adding all the 8 quantities. For each such polynomial obtained from a smoothed 3-SAT formula, with a little more work that we omit here, we can also assume that the coefficients of each monomial is an independent, uniform . We thus focus on strong refutation of semirandom homogeneous polynomials of the form:
(2)where , the instance hypergraph, is simply the collection of different sets of size (corresponding to each original clause) and are chosen uniformly and independently for each . Here, strong refutation involves certifying that for a sufficiently tiny .
2.1 From Quadratic Polynomials to Matrices
Let us show how spectral methods show up by starting with the simplest setting of . Then, each is a set of size 2, or simply a pair , and from (2) is a degree 2 polynomial in . The idea is to view such a degree 2 polynomial as a quadratic form.
For an matrix , its quadratic form on a vector equals . This expression is a homogeneous quadratic polynomial in . Indeed, every quadratic polynomial is a quadratic form of an associated matrix and vice-versa. For our , let the matrix be defined by:
Then, for any , .
A basic result in linear algebra allows upper-bounding any quadratic form of as:
where is the length of the vector and is the “spectral norm” or the largest singular value of . Since has -coordinates and thus length , we obtain that .
This bound on is easily verifiable. Given (obtained easily from the -SAT formula ), we form the matrix and use a linear time algorithm (called power iteration) to obtain good estimates on the spectral norm .
To certify , we need to check that . is an example of a random matrix since its entries are uniformly and independently distributed in . There is a well-developed theory for understanding the typical value of for such random matrices that allows us to conclude that where is the maximum number of non-zero entries in any row of the matrix . If the pairs are “equidistributed” that is, any variable participates in roughly the same number of pairs, then we would expect where is the average number of non-zero entries in a row of . Thus, which is if .
What if the set of pairs is not regular and some is “over-represented” in the set of pairs ? While we omit formal details, it turns out that one can use an elegant reweighting trick (discovered in the work of17) on the matrix that effectively allows us to assume regularity if .
2.2 Generalizing to Quartic Polynomials
The case of odd turns out to be technically challenging so let us skip and generalize the above approach when is of degree (that is, the case of 4-SAT). So, is not quadratic in . We will now view it as a quadratic form in variables each corresponding to quadratic monomials in the original assignment . Let us write for the vector in indexed by pairs with entry at given by . Define the matrix :
Then, as before, we can observe that:
The factor 6 comes from the fact that there different ways that a set of size 4 can be broken into pairs of pairs each of which arises as a term in the quadratic form above.
We can now write
And a similar appeal to results in random matrix theory tells us that with high probability where is the maximum number of non-zero entries in any row of . Equivalently, is the maximum number of 4-clauses that a pair participates in. When all pairs behave roughly similarly, we will have , in which case
with high probability if .
Early proofs of such facts used different tools from random matrix theory and worked for random 4-SAT by utilizing that is a random collection of 4-sets in that case. Our approach here explicitly reveals that only an equi-distribution (that is, ) property of is required for the success of this approach. This allows us, via a similar reweighting trick (that succeeds if ) discussed above, to obtain a result that works for arbitrary (worst-case) hypergraphs.
Let’s finish this part by noting our quantitative bounds. For , our refutation succeeded when . For , we instead needed . Indeed, for arbitrary even , a similar argument yields a bound of —a significant improvement over the clauses required for refuting an unsatisfiable -SAT formula in the worst-case, showing us the power of the spectral approach.
2.3 Beyond Basic Spectral Refutations
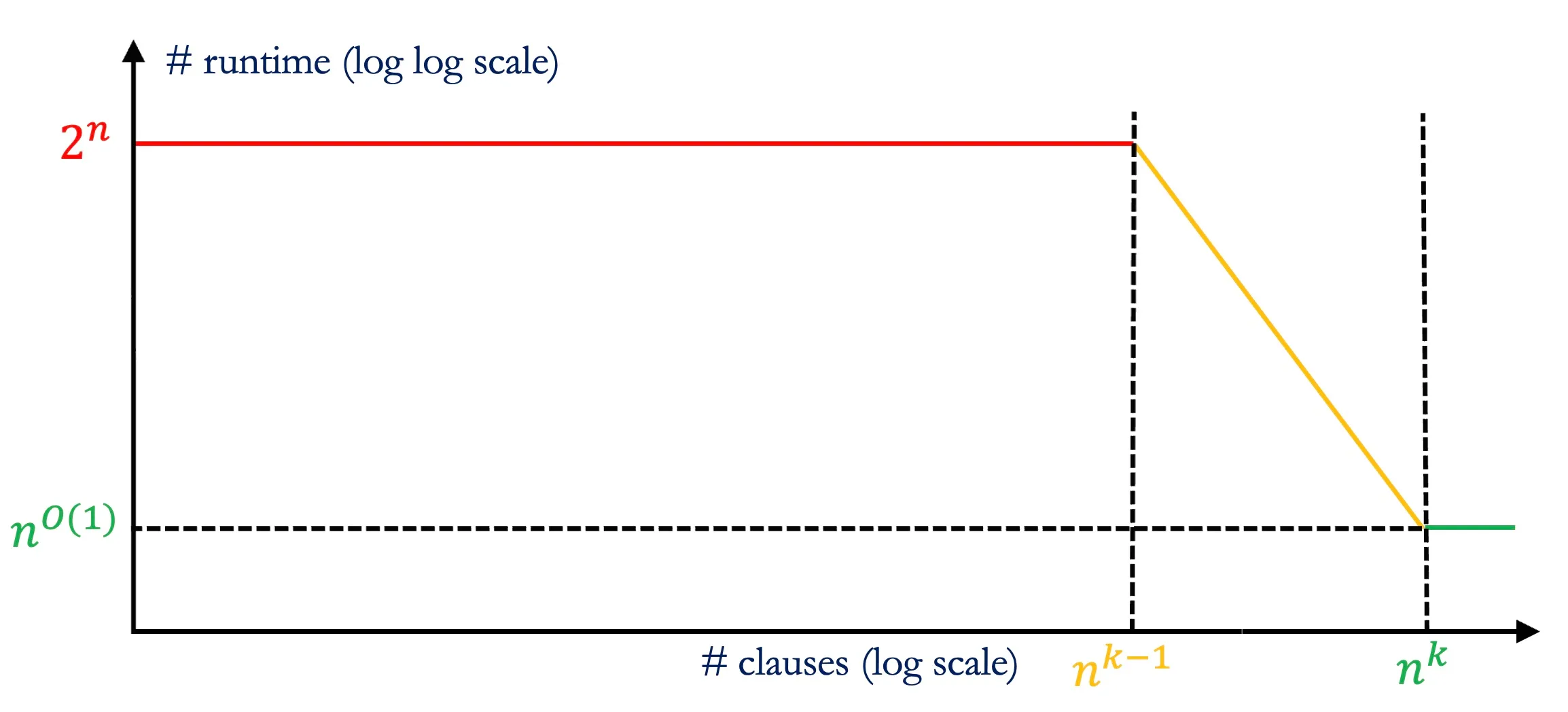
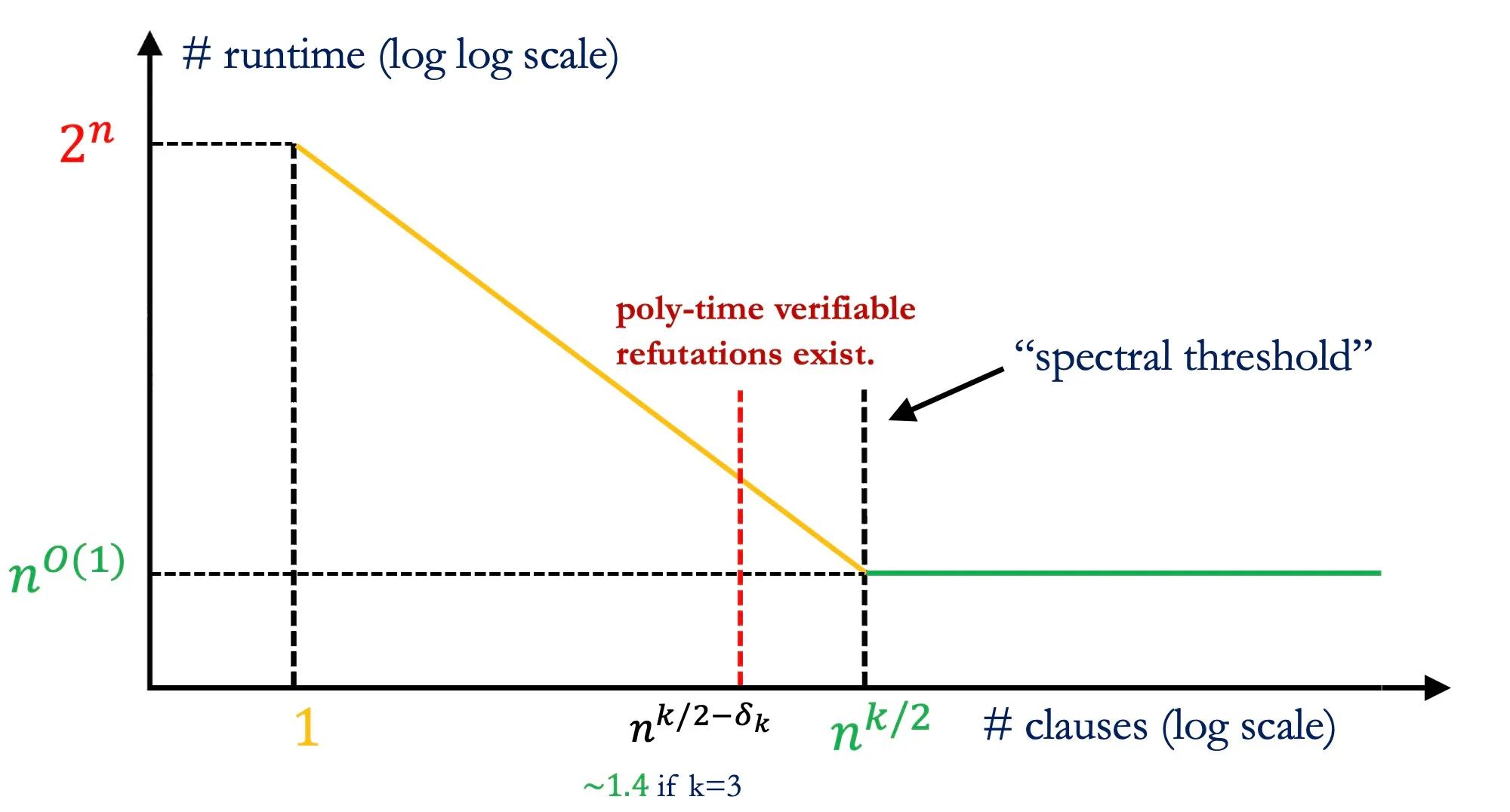
A smoothed -SAT formula is unsatisfiable with high probability whenever it has clauses. But our spectral refutations above require —a bound higher by a factor (and for arbitrary even ). This is because our approach fails whenever the average number of entries in a row of , that is, , is . The question of whether there are non-trivial refutations for -SAT formulas when (now called the spectral threshold) remained open for more than a decade and half. In the same time, researchers found evidence, in the form of restricted lower bounds,20 that there may be no polynomial time refutation algorithm for . This, nevertheless, left open the possibility of significantly beating brute-force search below this threshold. This possibility was realized for random-SAT in 2017. We will now discuss a significantly simpler (described essentially in full below!) spectral approach that succeeds even for smoothed -SAT.
We will continue to work with . As before, we will write as a quadratic form but instead of the natural matrices we discussed above, we will use Kikuchi matrices that we next introduce. First, though, a piece of notation: for sets , we let denote the symmetric difference of and .
For any , the level -Kikuchi matrix for is a matrix with rows and columns indexed by sets of size and entries given by:
Observe that for , the above Kikuchi matrices specialize to the matrix we saw in the previous subsection. Let’s see why is a quadratic form of .
For any assignment , denote by the -dimensional vector with coordinates indexed by sets of size and -th entry given by . Then, for we have:
Here, we used that since , for any , as for every . The last equality holds true because the number of pairs such that are -size sets and is exactly for any set of size 4. Observe how our notational trick of switching to -valued truth assignments paid off here.
Given this simple observation, we can now again construct the spectral upper bound . Furthermore, it turns out that powerful tools of random matrix theory still allow us to conclude as before that
(3)The Kikuchi superpower: Density Increment.
Why might this upper bound be better? The meat is in the density increment. As grows, the number of rows in grow. But the number of non-zero entries in grow even faster, giving us a net increase in . Indeed, let for some parameter . Then, since each contributes non-zero entries, . In particular, even when (and thus we have clauses) choosing large enough still allows us to obtain a .
Surprisingly, the rest of the proof idea is more or less the same as before! Let us assume, as we did at first in both the previous subsections, that all rows of have roughly equal number of non-zero entries. Such a condition holds true if is a random collection of sets of size 4. Then, . Plugging this back in (3) gives
if or . Since , this condition holds if .
Furthermore, as in the previous two subsections, we can use a variant of our reweighting trick to generalize this argument to arbitrary without any further assumptions. To verify this bound algorithmically (that is, to “check” our refutation), we need to construct the matrix and compute its spectral norm. This requires a run time proportional to the dimension of the matrix which scales as . So, all in all, we obtain a roughly time algorithm to certify that whenever for any . When for some small , that is, even slightly superlinear, the runtime of our algorithm is strictly sub-exponential (specifically ) and thus asymptotically beats brute-force search.
Handling odd k: We described our approach so far for even . The case of odd turns out to be a little more involved. This has been true for spectral algorithms ever since the earliest spectral algorithms for the problem. The polynomial time case (for example, when for 3-SAT analogous to for 4-SAT) were first found in a work of Abascal, Guruswami, Kothari in 2021. The full trade-off required introducing the correct generalizations of the Kikuchi matrices that we have described above. The analysis of the spectral norms of such matrices requires more effort and some additional combinatorial ideas.
We will not formalize these ideas here but note the following eventual result that we derive as a consequence:
For any and , given a semi-random homogeneous degree polynomial with non-zero coefficients, there is a time spectral algorithm that certifies . Consequently, for any , we can refute smoothed -SAT formulas with clauses also in time .
3. Proving Feige’s Conjecture
Let us now see how our spectral algorithms for smoothed -SAT provides a resolution for Feige’s conjecture. Our approach can be thought of as a theoretical equivalent of encoding the search for a proof into (un)-satisfiability of a SAT formula and then running a practical SAT solver. Given a hypergraph , we will build a SAT formula that will be satisfiable if does not have a short cycle. We will then prove that is in fact unsatisfiable to complete our proof. Of course, instead of using the computer to find such a refutation, we will “find” them (that is, argue their existence) analytically by appealing to our spectral algorithms.
Let us now describe this our argument in more detail. We are given an arbitrary -uniform hypergraph on nodes and average degree . Our goal is to show that must have an -length cycle. Starting from , we will define a family of homogeneous degree polynomials:
Observe that is clearly satisfiable. Indeed, if for every then , the maximum possible value.
Our key claim below will argue, using the analysis of our spectral algorithm from above, that if has no short cycle then must in fact be unsatisfiable:
If has no length cycle, then, .
We thus immediately hit a contradiction unless has a length cycle.
Let us now discuss why Lemma 5 must hold for even . For , we let be the Kikuchi matrix for the polynomial that we built in the previous section:
Then, we have: .
We will now argue a rather odd-looking fact. Consider the polynomial defined below for arbitrary :
We also let be the special case when s are chosen uniformly at random and independently. Notice that has the same form as the polynomial we analyzed in the previous section. Let be the Kikuchi matrix built from :
We will argue that if had no -length cycle, then no matter what the value of ’s are. Now, from the previous section, we know that for random thus for every :
This claim can appear strange. How can it be that does not depend on the ’s at all? In a sense, our proof reveals how short cycles in are “necessary” for to be as small as it is in the previous section!
Trace Moments and Spectral Norms.
To relate and and to bring in the cycles in , we will utilize a classical connection between and the so-called trace moments of a matrix that, in turn, are related to a certain combinatorial count of walks on .
For any symmetric matrix , let be its singular values placed in descending order. The trace is simply the sum of the diagonal elements of . For any even , a classical observation in linear algebra says that the trace of the -th power of equals the sum of -th powers of its singular values:
This is helpful because we can now write:
That is, the -th power of equals up to a factor . By taking and taking -th powers on both sides and recalling that as gives:
Thus, for , is a faithful approximation to .
Relating and via Trace Moments.
Using the above connection, we will now focus on arguing that for . This would give us .
We now recall another classical observation from basic linear algebra that relates trace moments of a matrix to a certain combinatorial count of “walks” on . For (standing for or ), we thus have:
(4)That is, is the sum over all sequences of row indices (that is, subsets of of size ) of product of the entries of on consecutive elements of the sequence.
Every entry of is either 0 or and for each non-zero entry , for some . Thus, any -sequence that contributes a non-zero (and thus exactly in ) value to the sum above must correspond to a -tuple of hyperedges from , one for each entry .
More is true about such a , as we next demonstrate in the crucial observation below. Let be the 0-1 indicator of the set . That is, if and only if .
Any corresponding to a non-zero term in (4) satisfies mod 2.
This crucial observation is actually quite simple to prove. We know that mod 2 for every —since . If we add up all the left hand sides we get a sum over ’s where every appears exactly twice (since occurs in exactly two entries and ). Thus the left hand side (and thus also the right hand side) must add up to the 0 vector modulo 2.
Next, notice that the -th entry mod 2 if and only if occurs in an even number of ’s. Thus, the above observation says that the (multi)-set is a cycle or an even cover. This appears exciting since we have a direct relationship between and cycles in !
There is a crucial snag though—the same could recur multiple times in . Indeed, if for every or more generally, every appeared in pairs, then, of course every element will occur in an even number of ’s, for the trivial reason that the ’s themselves occur in pairs. Let’s call such -tuples trivial cycles—that is, the ’s occur in pairs and thus do not relate to cycles in .
Now for our endgame. For every trivial cycle, since ’s appear in pairs, the quantity has even number of copies of for every . Since , this quantity must equal 1 regardless of the ’s! Thus, no matter what the ’s, all non-zero terms contribute exactly 1. In particular, (where all ’s equal 1) must equal regardless of s.
This finishes our argument, but it’s perhaps helpful to summarize it: we related (for both and ) to . We then related to a sum over -tuples . The non-zero terms in this sum correspond to for for such that mod 2—this step crucially uses the structure of the Kikuchi matrices. If has no length cycles, then in every nonzero term in the sum the ’s must occur in pairs, in which case we observe that and is thus independent of what the ’s themselves are.
4. Even Smaller Refutations
In the final act of this article, we will come full circle to show how the purely combinatorial Feige’s conjecture yields a surprising corollary for refutations for -SAT. We discussed a spectral algorithm that finds refutations for smoothed -SAT whenever the number of clauses . Improving on this spectral threshold even for the substantially specialized setting of random 3-SAT has been open (with accumulating evidence that this maybe impossible) ever since the 2004 work8 that obtained first such result.
In a surprising twist from 2006, Feige, Kim and Ofek proved12 that for random 3-SAT formulas with clauses (significantly short of the spectral threshold of ) admit short, polynomial size refutations with high probability. That is, there exists a polynomial size certificate, based on a clever combination of spectral and combinatorial ideas, which, if given, can easily help convince us of its unsatisfiability. But despite around two decades of efforts, we do not know polynomial time algorithms to find such a certificate. The FKO result forces us to grapple with the possibility that there may be a marked difference between existence of short certificates for NP-hard problems and efficient algorithms to find them. No such gap is known (or expected!) for worst-case -SAT, making this a truly average-case phenomenon. And, no such gap is known for any other discrete optimization problem, even in the average case. Indeed, ever since its discovery, FKO has been a one-of-a-kind result with an aura of mystery around it.
Are the mysterious FKO certificates a quirk of the random 3-SAT model? Or should we expect analogs in more general instances? We will now sketch how our results from the previous two sections allow us a surprising corollary:
With high probability, smoothed 3-SAT formulas with clauses admit an easily-checkable polynomial size refutation. More generally, a similar result holds for smoothed -SAT formulas with clauses where depends only on .
That is, the FKO results extends without any quantitative change to smoothed 3-SAT formulas. The existence of short cycles in hypergraphs plays a major role in obtaining this corollary. Indeed, this was also a principle motivation for Feige’s conjecture back in 2008. At the time, since Conjecture 1 was not known, FKO’s proof used a sophisticated application of the second moment method from probability theory with rather complicated calculations. Given Theorem 2, our new certificate and its analysis will be simple.
The idea for construction such refutations is quite simple. Our spectral refutation worked by splitting the polynomial into 8 different polynomials of degree and then refuting each polynomial via our spectral algorithm. As before, we will do the splitting and use the spectral algorithm for all terms of degree , that is, for all except for the homogeneous degree 3 polynomial corresponding to the last term in (1) for which, we will use a “combinatorial” method. Importantly, for the degree terms, our polyomial time spectral algorithm from Section 2.1 only needs (instead of ) to certify a bound .
The basic observation behind the combinatorial method is rather simple. Let be the 3-uniform hypergraph of monomials appearing in . Let be a cycle in and let be the “fragment” of that only keeps the monomials corresponding to the cycle. Then, if (which happens with probability over the choice of ’s), then, we claim that for every . That is, every must in fact be at least 1 short of the maximum value of on such a fragment. Suppose not and say for some , . Then, for every . Thus, . But on the other hand, since is a cycle, every occurs in an even number of ’s and thus, . This is a contradiction!
Here’s how this basic observation helps. Suppose has hyperedges. Then, we know from Theorem 2 that contains a cycle. We can then remove the hyperedges in this cycle and repeatedly find length cycles in the residual hypergraph. This process gives us a “cycle partition” of of hyperedges of into cycles of length . From our argument above, for about of such cycles, the product of the corresponding ’s will turn out to be . Let’s call such cycles violated. Thus, can write:
For each violated cycle, every must “lose” at least 1 on the maximum possible value of the polynomial. So, we know that at any , must be short of its maximum value by at least the number of violated cycles in the partition. So, . This is a significantly weaker bound than that of our spectral algorithm (), but is still non-trivial. It is also efficiently verifiable given a list of violated cycles (of size at most , so polynomial size).
The corollary follows by combining this combinatorial certificate with the spectral bound on the degree parts of . The precise parameters are obtained by optimizing above but we will omit it here.
5. Conclusion
In this article, we surveyed a new class of spectral algorithms based on Kikuchi matrices to find refutations, that is, easily verifiable proofs of unsatisfiability, for smoothed -SAT formulas. The guarantees we obtained were as strong as the best-known (and conjectured optimal) ones for the substantially simpler random -SAT formulas and substantially surpass the best-possible (assuming standard hardness conjectures) running times for worst-case -SAT formulas at every clause density. The approach generalizes to yield similar results for all logical constraint satisfaction problems. We also saw the resolution of the 2008 conjecture of Feige on short cycles in hypergraphs as an example application. And as a consequence, we saw how to extend the one-of-a-kind Feige-Kim-Ofek result from random -SAT formulas to all smoothed -SAT formulas. Taken together, the results show that, per the current state-of-the-art, smoothed -SAT is no harder than the substantially simpler random -SAT formulas for both refutation algorithms and existence of short certificates.
The Kikuchi matrix method, the method of proving results by finding spectral refutations for a related propositional formula, coming out this line of work appears to be a promising new attack on problems in combinatorics and coding theory. It is a pleasing theoretical analog of the powerful approach for resolving mathematical problems via practical SAT solvers—a decidedly “computer science” approach to solve problems in mathematics. A few more applications, including making progress on some decades-old problems in the theory of local error correcting codes,4,19 are now already around and we anticipate more such results in the near future. (See Figure 2a and 2b.)



Join the Discussion (0)
Become a Member or Sign In to Post a Comment