
In the beginning, Internet pioneers dreamed of creating an open framework for global communication and interaction. It would be a place where free thinking and information could flourish. Over the last half century, despite a few potholes and speedbumps, the Internet has largely lived up to that promise.
However, there’s evidence that attitudes and values are shifting. Governments around the world are taking steps to limit access to information, or even shut it down using tactics like site blocking, URL throttling, restricting mobile data, and regulatory and legal threats.
“This is in the face of governments, business and industry, and popular movements responding to perceived threats to dominant institutions and traditional sources of information,” observes William H. Dutton, Emeritus Professor at the University of Southern California and co-author of the UNESCO report Freedom of Connection, Freedom of Expression.
Washington D.C.-based democracy advocacy group Freedom House reported in 2021 that Internet freedom declined for the fifth year in a row in the U.S. and the 11th consecutive year internationally. Officials in at least 20 countries suspended Internet access, and 20 regimes blocked access to social media platforms, the report noted.
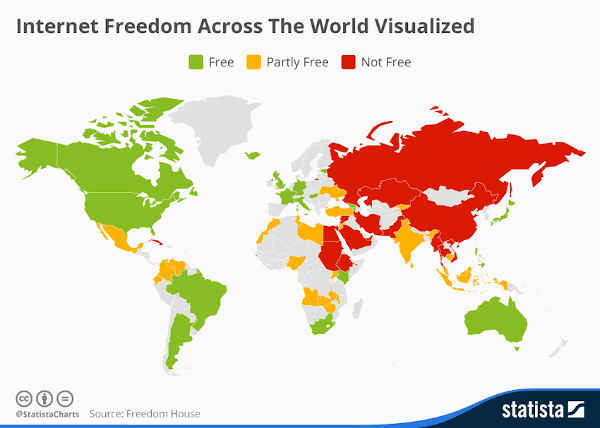
Credit: Freedom House
Says John Arquilla, Distinguished Professor Emeritus of Defense Analysis at the U.S. Naval Postgraduate School, “There’s a growing emphasis among some governments to curtail political freedom by using the Internet and social media to control thought and action.”
Out of Control
Internet freedom is eroding on two fronts: the sheer number of efforts to block access to legitimate information, and the level of sophistication used. According to Access Now, an organization that says it “defends and extends the digital rights of users at risk around the world,” 850 intentional shutdowns have taken place over the last decade, with 768 of these events occurring over the last five years.
Not surprisingly, countries such as Russia, China, Myanmar, and North Korea are typically associated with Internet restrictions. In Russia, for instance, all local ISPs route traffic through state-run central servers that can block it at any moment. However, the University of Michigan’s Censored Planet project found that Norway, Italy, Japan and other democracies also have taken the plunge. In 2020, India’s government shut off Internet access on at least 109 occasions.
In the U.S., the Trump Administration scrubbed and modified federal government websites to hide information about everything from climate change to healthcare access.
According to Jigsaw, a unit within Google that tracks controls and censorship, nation-states use six primary methods to impose full and partial Internet shutdowns:
- throttling or slowing down sites;
- IP blocking;
- mobile data shutoffs;
- DNS interference (a.k.a. cache or DNS poisoning , which involves an entity manipulating a specific URL);
server name identification blocking; and - deep packet inspection (DPI) that filters out undesirable content.
These techniques are more common in countries that have greater control of telecommunications infrastructure, Jigsaw noted.
However, technical approaches are not the only way to limit and control Internet access. The U.K. and U.S. also have inched in the direction of “censorship and surveillance,” Dutton says. This has included increased regulation through the Office of Communications (Ofcom) in the U.K. and FOSTA-SESTA human trafficking laws in the U.S. The latter led to ISPs and others shutting down personal ads and non-trafficking sites and services, but has resulted in few convictions for actual crimes.
Raising the Stakes
While methods exist for circumventing controls—including virtual private networks (VPNs) and specialized anti-poisoning tools such as Jigsaw’s Intra—most Internet users are not even aware of these tools, or they will not pay for them or take the time to set them up.
Some countries, such as Russia and China, are also banning these technologies. “There are growing controls over products and technologies sold and used in different countries,” says Sergey Sanovich, a postdoctoral researcher at the Center for Information Technology Policy at Princeton University. “We see countries blocking access to tools like VPN or demanding that private companies shut down or stop offering certain services and products that allow people to bypass controls.”
Dutton believes there is a fundamental need to refocus the discussion on core problems. He argues that user-generated content (UGC)—which he sees as critical to the Fifth Estate—has profoundly changed things. “Searching, creating, networking, collaborating, and—yes—leaking in the public interest” have upped the stakes—and instilled greater fear among leaders. What is needed, he says, is to shift the focus from the medium—typically UGC and social media—to the actual problem: malicious users.
Despite the recent decline in Internet freedom, many observers remain hopeful. Says Arquilla, “When you peer into the Internet, you’re looking at a vast wilderness. It isn’t surprising that nations would attempt to control and regulate it. This has occurred through history, particularly among authoritarian governments. But there’s a fundamental reality: people desire freedom and freedom usually wins out in the end.”
Samuel Greengard is an author and journalist based in West Linn, OR, USA.



Join the Discussion (0)
Become a Member or Sign In to Post a Comment