Lattice-Based Cryptosystems and Quantum Cryptanalysis
Security and Privacy
LLM Hallucinations: A Bug or A Feature?
On the Difference between Security and Safety
Safe networking requires us to be skeptical of messages that try to stampede us into action without enough forethought.
LLMs’ Data-Control Path Insecurity
We need to think carefully about using LLMs in potentially adversarial situations . . . like on the Internet.
The Dangers of Digitization, and The Importance of Data Backup
Maximizing Power Grid Security
Developer Ecosystems for Software Safety
Perspectives on AI from Around the Globe
In Memoriam: Ross Anderson, 1956-2024
The Risks of Source Code Breaches
The Return of Age Verification Laws
Will generative artificial intelligence accelerate the growth of made-for-advertising sites?
Device Onboarding Using FDO and the Untrusted Installer Model
The Science of Detecting LLM-Generated Text
A technical introduction to LLM-generated text detection methods.
Indistinguishability Obfuscation from Well-Founded Assumptions
We examine a formalization of the “one-way compiler" concept with the notion of indistinguishability obfuscation.
Technical Perspective: Hiding Secrets in Programs
"Indistinguishability Obfuscation from Well-Founded Assumptions," by Aayush Jain et al., gives a new construction of indistinguishability obfuscation that is provably secure.
Disinformation 2.0 in the Age of AI: A Cybersecurity Perspective
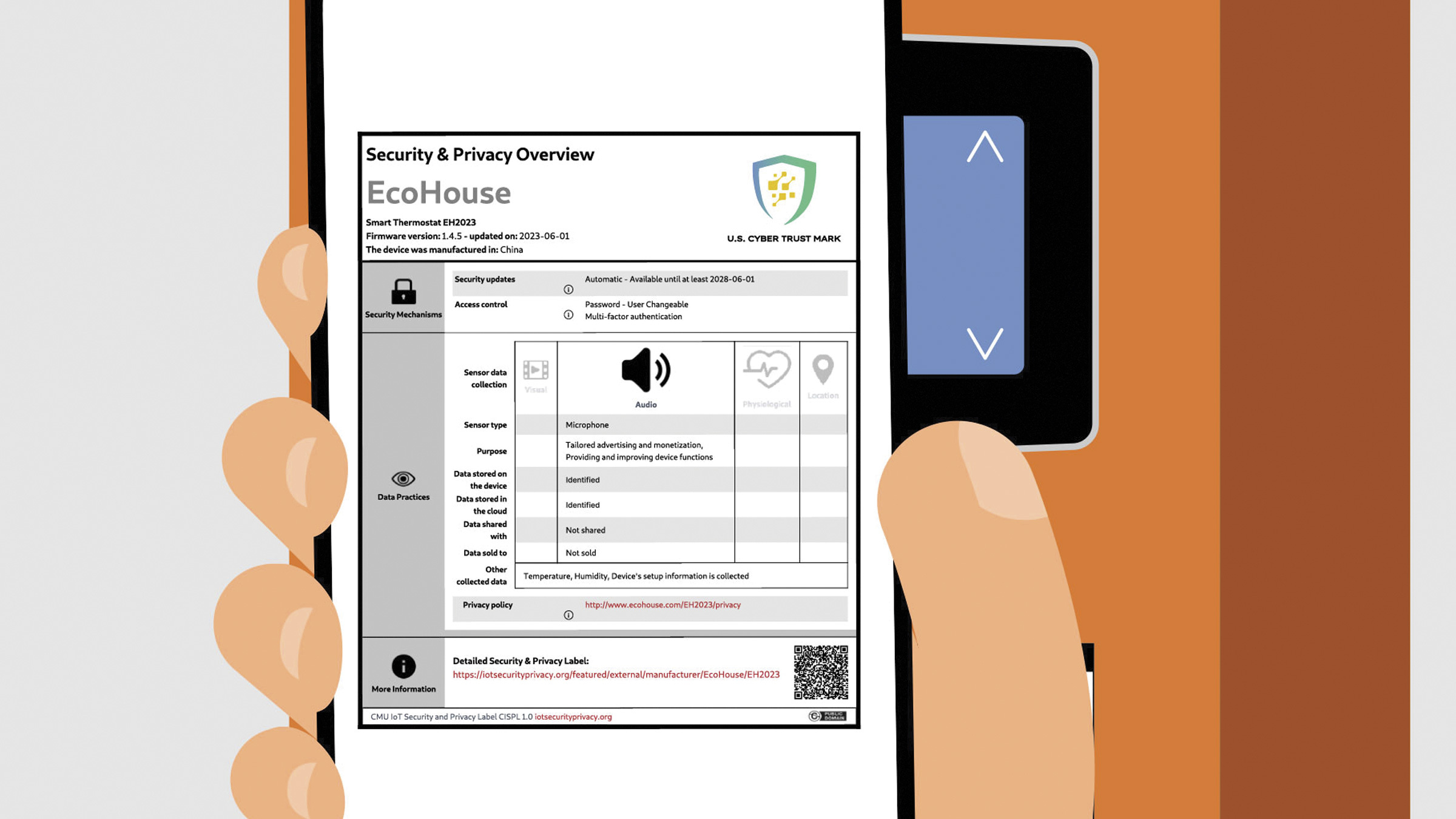
Internet of Things Security and Privacy Labels Should Empower Consumers
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get InvolvedCommunications of the ACM (CACM) is now a fully Open Access publication.
By opening CACM to the world, we hope to increase engagement among the broader computer science community and encourage non-members to discover the rich resources ACM has to offer.
Learn More