This paper seeks to make progress on the prevalence of popular security practices and their relationship to security outcomes via the longitudinal empirical measurement of a large population of computer devices.
Stefan Savage
Author Archives
A Fistful of Bitcoins: Characterizing Payments Among Men with No Names
Bitcoin has the unintuitive property that while the ownership of money is implicitly anonymous, its flow is globally visible. In this paper we explore this unique characteristic further, and consider the challenges for those seeking to use Bitcoin for criminal or fraudulent purposes at scale.
Privacy-Preserving Network Forensics
Privacy-preserving attribution of IP packets can help balance forensics with an individual's right to privacy.
Difference Engine: Harnessing Memory Redundancy in Virtual Machines
Virtual machine monitors are a popular platform for Internet hosting centers and cloud-based compute services. But main memory is not amenable to multiplexed hardware resources and is often a bottleneck in achieving higher degrees of consolidation.
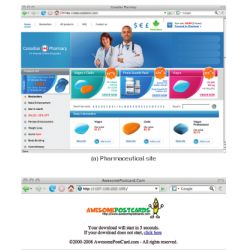
Spamalytics: An Empirical Analysis of Spam Marketing Conversion
We all receive spam advertisements, but few of us have encountered a person who admits to following through on an offer and making a purchase. And yet, the relentlessness by which such spam continually clogs Internet inboxes provides undeniable testament that spammers find their campaigns profitable.
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get Involved