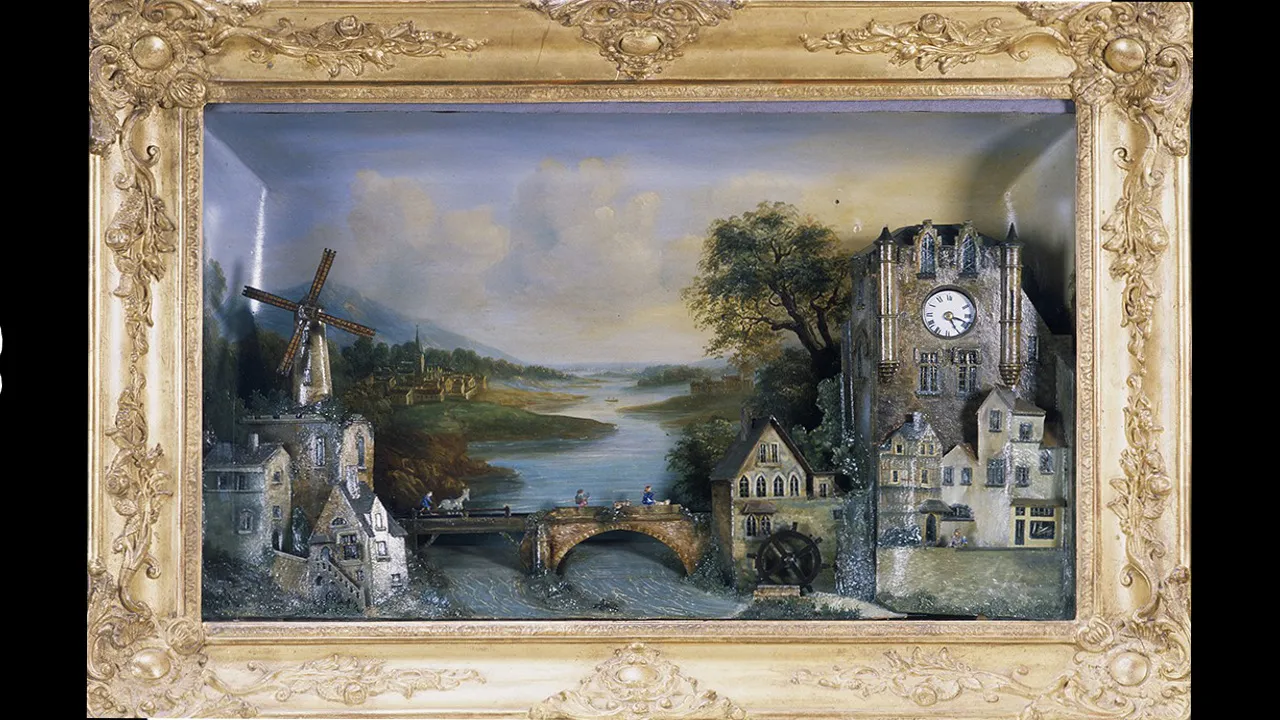Professionals must invest in continuous education to understand AI's potential, avoid pitfalls, and harness its benefits.
Erdin Beshimov
Strengthening Security Throughout the ML/AI Lifecycle
Automation, audits, and access control are some of the ways to enhance security in ML systems.
Zero-Trust Security in Software Development
The zero-trust security model is a proactive approach to overcoming potential threats and enhancing application security.
Computation and Deliberation: The Ghost in the Habermas Machine
People interacting only with the Habermas Machine to develop policy neglect the relational and interpersonal dynamics crucial to democratic deliberation.
AI-Driven Code Review: Enhancing Developer Productivity and Code Quality
AI-driven code review tools use deep learning and natural language processing to understand coding patterns and offer suggestions.
UPI 123Pay: India’s Innovation in Mobile Payments
The payment system was developed for India's 400 million users of simple feature phones instead of smartphones.
Integration of Music and Art in a Science and Engineering-Based University
How do technology researchers involved in music and art view its relationship with their science and engineering research?
From X to Bluesky: To Echo Chamber or Not to Echo Chamber?
Our desire to avoid cognitive dissonance makes us inherently susceptible to echo chambers, a phenomenon intensified by algorithms that curate what we see, creating an environment in which beliefs are seldom challenged.
Advanced Machine Learning Algorithms for HR Analytics
Technical Marvels, Part 9: Program-Controlled Musical Picture Clocks
Parts of the painting, such as people, animals, and windmills, move in some picture clocks.
Finding Roles in a Team with Generative AI
Generative AI can help an organization fill roles that are responsible for different parts of a project.
Datagram Forwarding Considered Harmful
Perhaps we need to look to forms of structured networking as a means of restricting and controlling the use of unstructured routing.
There are technological reasons why BlueSky is experiencing sharp growth in users and activity.
Heutagogy in Computer Science Education
Heutagogy is characterized by self-determined learning, where learners are not only involved in the learning process but are the primary architects of their educational journey.
Hopper kept a backwards clock on her wall to remind herself to think outside the box.
The Importance of Robust Documentation in Software Development
Without well-maintained documentation, even the most elegant codebases can become opaque, inefficient, and impossible to scale.
The Gift That Keeps on Giving to Apple and Google
Technical arguments for keeping or upending the current Apple and Google mobile app store systems.
Computational Thinking: The Idea That Lived
Computational thinking is the idea that has not only survived, it is now seen as more important than ever in an age of AI.
‘Cheat Engines’ and Copyright in Video Games in the EU
The Court of Justice of the EU finds it permissible to observe, study, and test a program to reveal the ideas and principles underlying its operation and reproduce the results of its execution.
Generative AI as an Icebreaker to Help Us Accept Other Ways of Thinking
The icebreaker tool uses Generative AI to reveal connections between users while maintaining the rigor of their specialist disciplines.
Strengthening Security with Attack Surface Management
The ASM approach is built upon a network infrastructure graph developed by engineers for investigative purposes.
How AI Is Helping Doctors Make Better Decisions in Healthcare
AI-based decision support systems are like working alongside a really knowledgeable colleague to confirm you’re on the right track.
Technical Marvels, Part 8: Historical Surveying Instruments
Geometrical instruments in the 17th century focused on measuring distances and heights.
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get InvolvedCommunications of the ACM (CACM) is now a fully Open Access publication.
By opening CACM to the world, we hope to increase engagement among the broader computer science community and encourage non-members to discover the rich resources ACM has to offer.
Learn More