A new generation of portable scientific instruments is taking shape, thanks to mobile processors and innovative data-gathering techniques.
Alex Wright
Author Archives
Amid growing outcry over controversial online videos, tech firms grapple with how best to police online advertising.
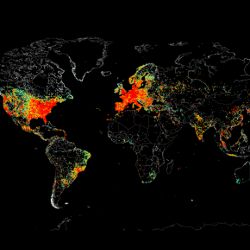
Mapping the Internet of Things
Researchers are discovering surprising new risks across the fast-growing IoT.
Search engine developers are moving beyond the problem of document analysis, toward the elusive goal of figuring out what people really want.
Security Experts Weigh in on Apple vs. the Fbi, Public Policy and the Law at Nyu Event
Most participants agreed the growing sophistication of security threats demands a shift from preventing attacks to detecting them as quickly as possible.
Natural Language Generation software begins delivering on the promise of automated prose.
Synthetic biologists may be closing in on potentially world-changing breakthroughs, but they are often hamstrung by a shortage of software tools.
Next-generation scientific instruments are forcing researchers to question the limits of massively parallel computing.
New ultra-fast wireless antennas may be on the way, but don't throw away your old wireless router just yet.
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get Involved