Industry 4.0 is enabled through the convergence of information technology (IT) and operational technology (OT) in industrial control systems (ICSs).2 At the core of Industry 4.0 are the cyber-physical systems (CPSs), such as power grids, manufacturing industries, autonomous vehicles, smart healthcare, and so forth connecting physical (OT) and cyber (IT) components through computational and networking capabilities.2 While CPSs facilitate automation and resource optimization, they introduce an expanded attack surface that spans both the cyber and physical domains.1 The evolution of tradecraft, from Stuxnet to Industroyer, on energy and utility infrastructure has shown the repercussions of such attacks on economic, business, and social sectors.5 Securing an operational CPS against potential attack vectors involves evaluating the system’s operational behavior and assessing security posture. To take security measures effectively, such assessments must occur without negatively affecting the ongoing operations, be reproducible for further investigation, and cover the system’s life cycle.2
Digital Twins: Security-Enhancing Enabler for CPS
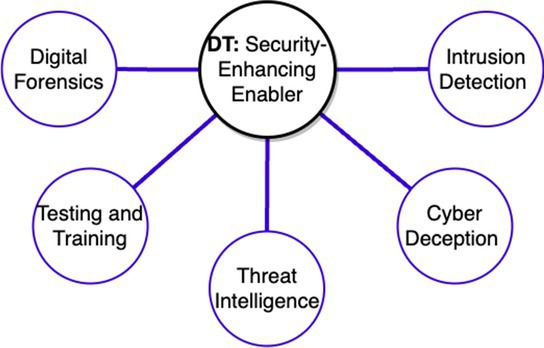
A digital twin (DT) is a virtual (digital) representation of the physical object or process that can replicate every facet of the underlying system along with its attributes, services, and interconnections throughout the system life cycle. With a continuous synchronized feedback loop between the physical counterpart (including CPS) and DT, the data flows from CPS to the DT, whereas decisions on the data including assessments, predictions, optimization, and calibration-related insights flow from the DT to the physical counterpart. DTs have gained significant attention in CPS as reconfigurable, reproducible, and economical non-disruptive simulation environments for security evaluation.2 Consequently, DTs have been realized as a complementary security-enhancing enabler in various cybersecurity solutions to reinforce the cybersecurity landscape, as Figure 1 shows. For instance, DTs can serve as intrusion-detection systems by continuously monitoring and analyzing data from the physical system against established behavioral baselines, promptly identifying deviations that could indicate intrusion attempts, and by enabling rapid response measures to mitigate potential threats.2 However, leveraging DTs without ensuring their trustworthiness could lead to abuse cases, making the concept of utilizing malicious DTs as a security-enhancing solution questionable.
Abuse Cases of DTs
A well-versed adversary can exploit benign behavior, digital-physical state synchronization, or building blocks (such as asset data, life cycle data, and modeling) of a DT to steer the CPS into an insecure state.6 Here. we focus on the potential perils of leveraging malicious DTs.
Garbage-in-garbage out (GIGO) problem.
DTs act as the primary source of data acquisition and dissemination for various data sources including physical assets, knowledge bases that comprise historical data, process knowledge for DT modeling, and other DT instance(s). Based on the data from these sources, DTs further evolve their security-enhancing capabilities and optimize the CPS services with each life cycle phase, ranging from design to end-of-life.6 With the chains of data to and from DTs, exploiting DTs may have severe consequences on the digital thread that links data across multiple DT instance(s) and system life cycle phases. Data adulteration through any digital thread may lead to a GIGO problem, where the model for the physical system no longer represents the system’s behaviour, leading to reduced DT utility. Such threads can be attractive targets to plot attacks, especially when manipulating high-valued design artefacts such as simulation models or where archived DT data can be used in next-generation processes.2
Information leakage.
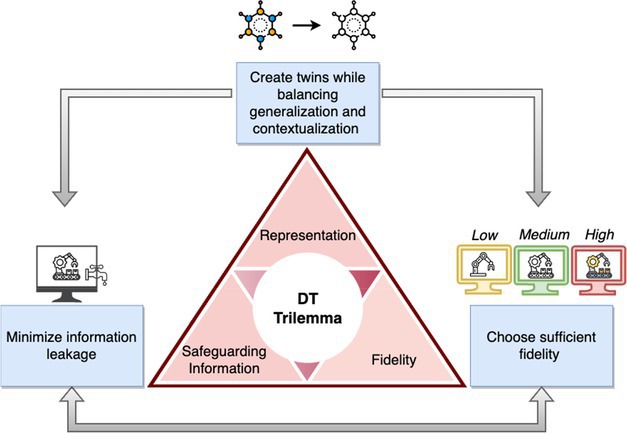
A precise representation of the system’s process knowledge through DT modeling is influenced by various considerations relating to information fidelity. Measuring the fidelity of a DT includes: (1) the degree of resemblance and synchronization frequency between physical space and virtual counterpart to register changes in terms of data, state, and model; (2) contextual abstraction; (3) resource considerations, such as monetary, computation, communication, or storage; and (4) the underlying security objectives of DTs3 as outlined in Figure 1. On one hand, a high-fidelity DT is essential to maintain replication accuracy. On the other hand, a high-fidelity DT, under attack, can cause inadvertent information leakage allowing an attacker to infer and codify the system’s process knowledge. This paradox leads to a DT trilemma involving representation, safeguarding information, and fidelity, as shown in Figure 2. The presence of a trilemma becomes evident when DT is used as a security-enhancing enabler. For instance, DT as a cyber deception platform must provide plausible-looking yet misleading information to deceive and engage adversaries. This property could be achieved through variable fidelity, typically medium-to-high fidelity. However, such deceptive attack surface settings can reveal significant knowledge about the system2 leading to information leakage of both the physical asset and its twin. Thus, addressing the trilemma in DT necessitates an abstraction-context trade-off for the underlying use case concerning the security objective of DT.
Passive disruption.
DT can be exploited as an attacker playground to covertly and passively observe and learn physical system behavior through DT models, (re)instantiate DT instances to analyze the system’s expected behavior and infer states through automatic feedback loops to and from the physical system. To passively compromise CPS, attackers can also manipulate user-specific configuration parameters to skew the simulation or delay state synchronization to cause desynchronization of the digital-physical mapping. Thus, attackers can passively disrupt CPS data, resources, or services by sabotaging DTs. Such command and control strategy also allows attackers to target CPS to disrupt DT services.6
Cascading inconsistencies or failures.
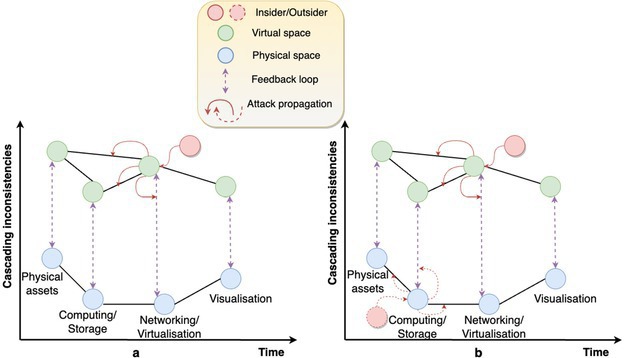
Based on the attacker’s motives and capabilities, including colluding with insiders, they can establish a persistent foothold in the physical and virtual space concurrently. This is referred to as a hybrid attack6 where attackers may choose cyber, physical, or cyber-physical domains as attacking surfaces to launch cascading inconsistencies or failures enabled due to feedback loops among the physical and virtual environment. Figure 3 illustrates that the spread of a hybrid attack (part b) is more significant as compared to the attack on either of the entities (part a), that is, physical or virtual spaces. Launching a sophisticated hybrid attack may involve considering the pre- or post-existence of the CPS-DT spaces, that is, targeting a pre-existing DT to adulterate CPS during the system design and engineering phase or vice versa. Furthermore, to sow chaos in a system of systems, attackers can launch an expanded attack with optimal living-off-the-land opportunities, that is, without using any illegitimate software and functions to perform malicious actions while maximizing disruption or destruction of data, resources, or services.
Maximization of threat landscape.
The creation, deployment, and operation of a DT can be realized through various technologies and infrastructures, which could be prone to attacks, including information technology platforms (CPS, Internet of Things), computing and storage (cloud-fog-edge computing), communication networks and virtualization services (5G/6G, software-defined networks), visualization and data analytics (big data, artificial intelligence/machine learning).7 The confluence of these technologies and interaction between physical, cyber, and cyber-physical realms unleashes a myriad of attack vectors that eventually undermine the accuracy and quality of a DT.1 For instance, rogue physical assets may act as a springboard to carry out transitive attacks on DTs. Similarly, tampering with data, resources, or services in the cyber-physical domain may lead to disruption of services in the DT space.
Reflections
DTs are typically designed to accurately represent physical systems. Such endeavours usually face the challenge of the inability to model all aspects of a physical system at high resolution. Security concerns introduce a new dimension for DTs. Modeling high-fidelity DT can be a double-edged sword. Benign DT can be leveraged for a range of reasons including, but not limited to, optimization, prediction, scale-up, as well as security enablement in any domain in general and CPS in particular. However, malicious DTs can potentially interrupt digital threads of physical counterparts, lead to information leakage, and expose the functioning of the physical system, including its data, resources, and services. These vulnerabilities allow cyberattackers to compromise and disrupt the operations of the physical system, thus posing a significant threat to the integrity of the entire CPS. Therefore, the following countermeasures should be enforced from the initial design and engineering phase of DTs to mitigate the perils of malicious DTs.
First, design a variable fidelity DT, that is a sufficient fidelity DT that maintains a balance between generalization and contextualization with minimum information leakage while realizing the security objectives of the underlying use case. Second, design resilient and context-aware DTs capable of directing the system under attack to enter a fail-safe state. With fault tolerance support, DTs must localize the compromized component(s) and allow the system to fail over to a replica or default state, where through DT versioning, the system state can be restored. Furthermore, the system must continue to provide a minimum level of functionality in the face of compromise or malfunctioning. Third, there must be a way to validate all the inputs to the DT and a transparent mechanism to validate the outcomes of the processes taking place within the DT. In other words, input validation and verification as well as DT outcome verification must be part of the DT operation life cycle.
While DTs provide opportunities and risks, understanding the risks and mitigating them through the proposed approaches can support the use of DTs more securely and effectively.




Join the Discussion (0)
Become a Member or Sign In to Post a Comment