Engineering Trustworthy Systems: A Principled Approach to Cybersecurity
Security and Privacy
Heterogeneous Von Neumann/Dataflow Microprocessors
Countering the Negative Image of Women in Computing
The Limit of Blockchains: Infeasibility of a Smart Obama-Trump Contract
Deep Insecurities: The Internet of Things Shifts Technology Risk
Enterprise Wi-Fi: We Need Devices That Are Secure by Default
APIs, Standards, and Enabling Infrastructure
Quantum Hype and Quantum Skepticism
Implementing Guidelines for Governance, Oversight of AI, and Automation
An Emerging Threat, Hiding in Plain Sight
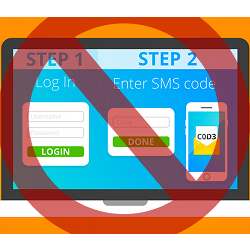
The Problem with SMS Two-Factor Authentication
Pondering Variables and Direct Instruction
HiPEAC: A European Network Built to Last
Cyber Security in the Quantum Era
New European Data Privacy and Cyber Security Laws: One Year Later
Enterprises Lead ICT Innovation in Europe
Welcome to the Europe Region Special Section
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get InvolvedCommunications of the ACM (CACM) is now a fully Open Access publication.
By opening CACM to the world, we hope to increase engagement among the broader computer science community and encourage non-members to discover the rich resources ACM has to offer.
Learn More