Technical Perspective: On Proofs, Entanglement, and Games
Security and Privacy
Post-Quantum Cryptography: Protecting Today from Tomorrow
Technical Perspective: The Real-World Dilemma of Security and Privacy by Design
Competitive Compatibility: Let's Fix the Internet, Not the Tech Giants
The Role of Professional Certifications in Computer Occupations
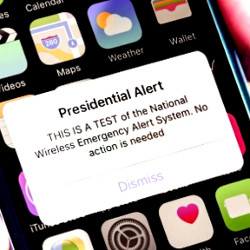
Securing the Wireless Emergency Alerts System
Dialing the Trust Level Down to Zero
Mining Financial Data Without Actually Seeing It Can Detect Fraud
How Music and Programming Led Me to Build Digital Microworlds
Photonic Processors Light the Way
Protecting the Global Internet from Technology Cold Wars
Testing Educational Digital Games
Quantum-Safe Trust for Vehicles: The Race Is Already On
A discussion of concerns on quantum vulnerability for the automobile industry.
Managing IT Professional Turnover
The Sand-Heap Paradox of Privacy and Influence
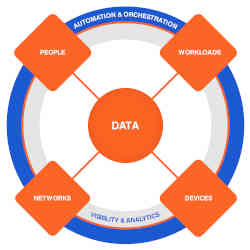
An Internet of Things Service Roadmap
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get InvolvedCommunications of the ACM (CACM) is now a fully Open Access publication.
By opening CACM to the world, we hope to increase engagement among the broader computer science community and encourage non-members to discover the rich resources ACM has to offer.
Learn More