Securing the Enterprise When Employees are Remote
Security and Privacy
The Making of an IT Strategy Consultant
Technical Perspective: Physical Layer Resilience through Deep Learning in Software Radios
Technical Perspective: The Effectiveness of Security Measures
These Are Not the Apes You Are Looking For
Let Us Not Put All Our Eggs in One Basket
Deploying Decentralized, Privacy-Preserving Proximity Tracing
When SDN and Blockchain Shake Hands
Protecting Children’s Privacy Online
DevSecOps: Resolving Disagreements Between Developers and Security Teams
A History of One Brute-Force Attack
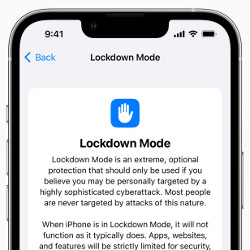
Extreme Security for Users Targeted by Cyberattack
Advances in the Quantum Internet
Color Blind Accessibility Manifesto
Why Universities Must Resist GPA-based Enrollment Caps in the Face of Surging Enrollments
Computational Thinking in the Era of Data Science
Shape the Future of Computing
ACM encourages its members to take a direct hand in shaping the future of the association. There are more ways than ever to get involved.
Get InvolvedCommunications of the ACM (CACM) is now a fully Open Access publication.
By opening CACM to the world, we hope to increase engagement among the broader computer science community and encourage non-members to discover the rich resources ACM has to offer.
Learn More