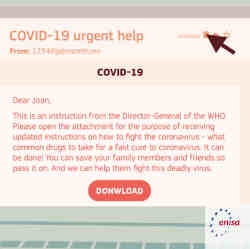
Cyber-thugs are relentless. They jump on the slightest dent in your data-protection armor and pry until something pops out. One of the latest cracks in cybersecurity is susceptibility to COVID-themed phishing attacks.
Cybercriminals load phishing emails and texts (smishing attacks) with COVID-19 alerts to lure people into clicking on malicious links and attachments. Criminal hackers are banking on people's COVID fears to scare them into clicking for test kits, vaccine registrations, and communications with contact tracers. The pretexts are new, but endgames, such as stealing user PII (Personally Identifiable Information) and credentials, and squeezing businesses and consumers for ransomware payments, remain.
Not to worry. There are tips and tools for dealing with these attacks, so people can reject false offers and alarms and keep their private data and finances intact.
In many attack campaigns, perpetrators such as nation-states and eCrime groups impersonate healthcare organizations. Hence, people think they hear from legitimate pandemic experts.
In a recent example, last December criminal hackers leveraged the Rhode Island Department of Health in a vaccine-themed phishing attack. The phishing message appeared to come from Dr. Kimberly Turner of the Rhode Island Department of Health, and alerted consumers to a fraudulent COVID vaccine pre-registration form using an infected link. "The form collected PII. The cybercriminals sold it by the thousands to other scammers to use in financial fraud," says Yochai Corem, CEO of Israel-based security startup Cyberint.
Other COVID phishing content offers medical tests, luring consumers to click and hand over money or information in hopes of receiving a coronavirus test kit. "The cybercriminals simply steal the victim's money, or obtain their credit card or other PII and sell it in the underground market on the dark web," says Jon Clay, director of global threat communications at TrendMicro.
Still other phishing attempts include notices that the user may have been infected, with links to more information. These scams pretend to perform contact tracing, frightening individuals into action because they believe their contacts may have infected them. However, the links allow the scammers to steal the private or financial data that people enter. "Most contact tracing is by a phone call or text; never by email," says Karen Panetta, IEEE Fellow and dean of Graduate Engineering at Tufts University. According to the U.S. Federal Trade Commission (FTC), texts from contact tracers serve only to alert people to receive a call; the agency warns you should never click on a link purporting to be from a tracer.
Further, the U.S. Federal Communication Commission (FCC) warns against believing or acting on COVID text message scams in general, which also may offer cures and warnings about the need for a test. Consumers should not click on links in texts related to the virus.
Cybercriminals phish businesses, too. Some COVID phishing approaches target organizations using Business Email Compromise (BEC) attacks that stress urgency in transferring funds out of the organization. Other attacks may take the form of spear-phishing, or reaching out to specific high-profile executives.
Flavio Aggio, chief information security officer for the World Health Organization (WHO), says that organization has seen the following examples of COVID-themed attacks:
- Business Email Compromise (BEC): The attacker compromises a user account at a pharmaceutical company, then uses it to send phishing messages to organizations like the WHO. Eventually, a plausible email chain emerges between the two organizations, with the criminal hacker gaining control of higher-ranking accounts. Then the attacker, posing as someone in authority at the pharmaceutical firm, requests an immediate funds transfer, to an overseas supplier, for example, but the bogus supplier receiving the funds is the cybercriminal.
- Targeted spear-phishing: The attacker poses as someone, a journalist perhaps, requesting an interview with the targeted executive on a COVID-related topic. The executive unwittingly downloads a malicious file later on in their exchanges, which gives the "interviewer" access to his or her network.
Cyber-hoodlums launch COVID-19-themed ransomware attacks against businesses. In one case, phishing attacks, including promises of vaccines, led employees to click on links and attachments that cough up malicious software. "These malware attacks can gain control of a typical employee's computer to use it as a starting point to move laterally across the network. That's how cybercriminals look for critical systems, datacenters, and cloud infrastructure to encrypt with ransomware," says Clay.
According to Clay, cybercriminals also can initiate ransomware attacks by gaining control of an executive's computer using a phony Microsoft Office 365 login screen. When the executive clicks the phishing link or attachment, Office 365 appears; once they log in to the Office 365 clone, the cyber-thugs capture the credentials used and log in to the company's genuine Office 365 program. The criminal hackers then send emails that appear to come from that person, spreading phishing attacks across the organization and capturing more credentials. The criminals may gain and sell access to the company's critical systems on the dark web, or insert ransomware to leverage the company for payment. "In Q1 2020, we saw average ransomware payments of $1.3 million," says Clay.
Cybercriminals send ransomware attacks to consumers, too. Whether it's the promise of a vaccine or test kit, the bait hooks them, they click, and the ransomware encrypts their files until they pay the scammer's price.
Curing COVID-19 phishing attacks, malware infections
Fortunately, most phishing comes with telltale signs. "The first red flag that it's a phishing attack is that the email or text was unexpected," says Panetta. If the sender appears to be a friend, colleague, or reputable organization, contact them directly, apart from the phishing message, and ask whether they sent it. Business users can forward suspicious emails and texts to their IT security group for closer examination.
Consumers who fall prey to phishers can alert the affected bank or credit card firm. "Freezing your credit is also important," says Panetta. Consumers who freeze their credit preemptively gain an edge against phishers.
People also can use Internet security products that support email scanning, and web reputation checking and scanning. According to Clay, if one clicks on a link that takes them to a malicious web server, such products can detect and block known bad websites.
Newer email security products for businesses and consumers have advanced detection technologies utilizing artificial intelligence as well, says Clay. "These technologies detect threats using rules and models garnered from investigating many similar types of attacks. They analyze the entire message in real time, including email header details, message content, and attachments," says Clay.
The WHO's Aggio suggests businesses should use Multifactor Authentication (MFA) and Endpoint Detection and Response (EDR). MFA ensures attackers need more than the passwords they've phished to log in on business systems. EDR can detect and delete malware. Organizations should prefer state-of-the-art EDR tools that identify ransomware attacks.
Aggio says the WHO also uses the DMARC (Domain-based Message Authentication, Reporting, and Conformance) email security control to fight email spoofing. He recommends the use of such control.
COVID-themed phishing isn't going away, at least until after everyone gets vaccinated. By mixing the right security tools and common sense and learning the earmarks of phishing, businesses and consumers can skirt most attacks and minimize suffering from those that do get through.
David Geer is a journalist who focuses on issues related to cybersecurity. He writes from Cleveland, OH, USA.



Join the Discussion (0)
Become a Member or Sign In to Post a Comment