
Ironically, the only part of the Internet that is secure today is the DarkNet, where hackers encrypt traffic, hide their identities, buy/sell stolen secrets, and even chit-chat about how to pull-off the latest scams. Public Internet traffic, on the other hand, is (by default) unencrypted (ClearNet, in hacker-speak).
Harvard University researchers claim to have uncovered the “missing link” towards an unhackable quantum Internet that one-ups the security of the DarkNet. By correcting for the signal loss in today’s quantum key distribution—its Achilles heel—these researchers have demonstrated a prototype quantum repeater that allows the long-distance transmission necessary for an unhackable quantum Internet.
According to Josh Nunn, a reader in the department of physics of the Center for Photonics and Photonic Materials at the U.K.’s University of Bath, “Quantum key distribution is already commercially available, but extending the working distance has been a long-standing research challenge because this requires ultra-strong light-matter interactions.” Nunn said the Harvard research team ” has brought together multiple cutting-edge techniques to enable this for the first time, and have directly shown its applicability to this challenge. What is even more exciting is that these techniques could be applied more generally in areas such as quantum metrology and ultimately to quantum computing.”
The key to the quantum repeater invented by Harvard graduate students Mihir Bhaskar, David Levonian, Bart Machielse, Christian Nguyen, and Ralf Riedinger is its quantum memory cell, which was created by removing a carbon atom from a diamond lattice and replacing it with a silicon atom. The quantum state (qubit) of a single photon can then be transferred (using entanglement) to the silicon atom, and in so doing revealing (using teleportation) whether the qubit is the same or different from the initial state of the memory. Using a 10-step algorithm (spelled out in the authors’ paper), this quantum memory can be used to transfer a cryptographic code to make the transfer of ordinary traffic over existing Internet fibers unhackable, merely by augmenting its conventional repeaters with the Harvard quantum repeater.
“The underpinning technology for memory-enhanced quantum communication is truly remarkable,” said Wolfgang Tittel, a professor on the faculty of electrical engineering, mathematics, and computer science at the Delft University of Technology (TU Delft) in the Netherlands. “The work shows for the first time that the use of quantum memories makes quantum communication schemes more efficient than quantum communication schemes without such memories. Even though a lot remains to be done, it is clearly a milestone along the path to a world-wide quantum Internet.”
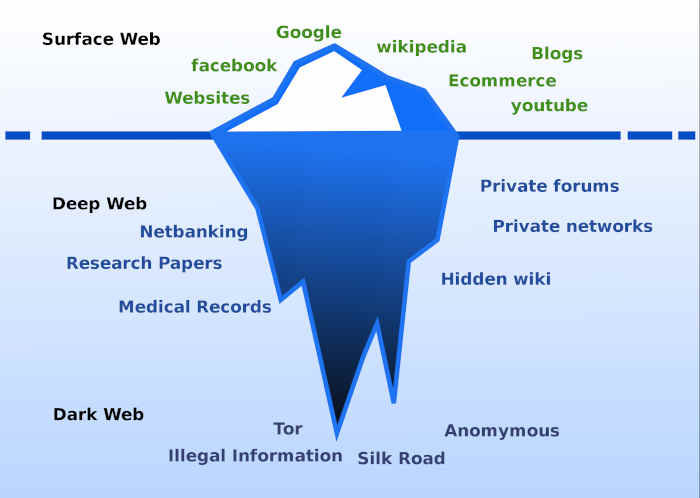
The DarkNet (bottom) is more secure than the ClearNet (Surface- and Deep-Web)
because its traffic is protected by hackers using encryption, unique protocols and anonymity proxies.
Credit: Wikimedia Commons
In more detail, the final steps to enable using Harvard’s quantum memories in a quantum Internet include optimizing the current prototype, as well as incorporating low-loss optical elements for routing photons to and from the memory node, adding frequency conversion hardware, and engineering algorithmic enhancements including decoy state protocols to prevent photon number splitting (PNS) attacks. These enhancements, according to the Harvard researchers, are all within reach of its current design.
“Our quantum repeater design is well-suited for deployment in real-world settings over distances of 350 kilometers [over 200 miles with over 10 miles between repeaters],” said Machielse, who worked with Harvard professors Marko Loncar and Mikhail Lukin. “Topologically, a single device can also be shared at the center of a star network enabling quantum communication among several parties beyond the metropolitan scale.”
According to the researchers, their quantum repeater can be extended using polynomial scaling of the communication rate with distance. In addition, multi-photon gate operations also will enable more rapid quantum communication, as well as realizing scalable quantum networks beyond quantum key distribution to quantum metrology and modular quantum computers.
“There is a lot a hype about quantum technology; many think it will make a big difference very quickly,” said Machielse. “But by studying the many challenges that may take a decade or more to develop, we found an area that actually could make a big difference quickly: namely, secure point-to-point quantum communications. The missing link, we found, was a quantum version of the analog repeaters used today.
Other researchers cited in their paper (Experimental demonstration of memory-enhanced quantum communication) have been trying to build reliable quantum repeaters for decades, but the Harvard researchers are the “first group that ever used a quantum memory to enhance communications,” said Machielse. “Many knew that quantum key distribution required the transmission of single photons, but our method of storing one photon’s qubit until the next photon arrives is a new approach to communications over long distances.”
In their prototype, the qubit value of the photon is stored for just 20 microseconds, but by optimizing parameters and making improvements currently underway, the coherence time of stored qubit values will last nearly a millisecond, the researchers say, enabling the cited long distances between quantum repeaters.
Two aspects stand out as making a quantum Internet the ultimate in security:
- First, the security of quantum qubits. In contrast to conventional digital bits, qubit values cannot be eavesdropped upon without destroying them. In fact, eavesdropping is detected by Harvard’s quantum repeater as a failed memory operation. In normal use, some failures are to be expected, which is why repeaters are needed in the first place (if values are always transmitted correctly, then the distance is close enough to not require a repeater). Thus both conventional analog and quantum repeaters use error-correction methods to identify failed transmissions.
- Secondly, the quantum repeater is merely measuring whether the stored-in-memory qubit is the same or different from the next one to arrive. In successful transmissions, the repeater broadcasts whether the qubit was the same or different to both the sender and the receiver, but not its actual value. When enough successful transmissions have been made, both the sender and receiver can sift out an unhackable secure key (a “one-time pad,” in cryptographer-speak).
The unhackable secure key then is used to encrypt Internet data transmissions over ordinary fibers using traditional analog repeaters that are in place today. Because the secure key is an unhackable one-time pad, it is impossible to decrypt even for future quantum computers.
The Harvard researchers will test their algorithm and hardware implementation over a fiber network on the campus of the Massachusetts Institute of Technology (MIT). They claim their prototype already is faster than today’s Rivest–Shamir–Adleman (RSA) public-key cryptosystems, and more efficient than single-photon encryption keys being transmitted today over distances short enough to not require repeaters. They also say that improvements already underway will enable future quantum repeater qubit memories to retain coherence for up to a full second.
“We believe that our quantum repeater hardware and algorithms for unhackable keys is the first way forward to building a usable, scalable quantum Internet,” said Machielse.
He adds that the prototype hardware and algorithms can be repurposed to improve the accuracy of the global positioning system (GPS), as well as enabling easier-to-use cloud-based quantum computing, since on-site computers will be able to carry on unhackable communications with quantum computers in the cloud.
R. Colin Johnson is a Kyoto Prize Fellow who has worked as a technology journalist for two decades.



Join the Discussion (0)
Become a Member or Sign In to Post a Comment