At the International Conference on Cyber-Physical Systems (ICCPS 19) last month in Montreal, Canada, researchers turned the tables on drive-by-wire automobile hackers. Using covert channels to defeat hackers trying to take over the steering, brakes, and other critical parts of modern cars remotely, the researchers demonstrated the hackers' own methods can be used to authenticate each individual command given over the vehicle's control area network (CAN), eliminating the possibility of unauthorized interference with the car's operation.
Office of Naval Research (ONR) program manager for Cyber-Physical Systems (CPS) J. Sukarno Mertoguno said the researchers, from the University of Washington in Seattle and the University of Padua in Italy, "developed a novel method for authenticating CAN bus transmissions. Taking advantage of a property of CAN bus protocol, they devised two timing-based and one storage-based covert channel; each, or a combination of them, can be used to carry the authentication tokens. The authentication methods and the covert channels together form a practical and efficient technique for bolting on security to a legacy CAN bus."
The CAN bus was not designed with built-in authentication, since it was originally a closed bus. Modern vehicles, on the other hand, use infotainment, navigation, and other services that have opened the CAN to wireless signals. Hackers have demonstrated they can take over a vehicle by a wireless intrusion using these channels; in response, the Washington and Padua researchers have demonstrated they can eliminate hacker access with a retrofit that uses covert channels to piggyback authentication signals atop the CAN bus.
"Covert channels usually refer to a type of cyber-attack that maliciously transfers information by exploiting the communication channels that are not intended for information transfer," explained University of Washington researcher Xuhang Ying. "The attackers gain unauthorized access to the CAN bus through indirect physical access—for example, the mechanics diagnostic port—or remotely through wireless access over cellular, Bluetooth, or Wi-Fi. We demonstrate the use of covert channels for automotive CAN buses; specifically, we propose TACAN (Transmitter Authentication over CAN), a system which turns upside-down the typically malicious concept of covert channels and exploits it to build an effective defensive technique that allows an electronic control unit to communicate authentication information."
Modern vehicles use dozens of electronic control units (ECUs) to eliminate the more costly mechanical coupling of steering wheels, brake pedals, and other physical controls in favor of sending commands electronically to the brake's calipers, the wheel's rack-and-pinion steering, and other vehicle actuators. The CAN bus eliminates the need for hardwired connections between controls used by the driver and the vehicle's actuators; instead, drive-by-wire vehicles use ECUs to collect input from the driver's wheel, pedals, levers, and buttons, and output commands over the CAN bus to the ECUs controlling the vehicle's actuators, triggering a response.
What the Washington and Padua researchers have done is elevate the security of the CAN bus with authentication to prevent hacker attacks by invalidating inauthentic commands, while simultaneously allowing all genuine commands to function properly. The cherry on the top is that, since the security authentication protocols run on the hackers' own covert channels, it consumes no excess ECU cycles that could slow down the CAN, but merely degrades the quality of legitimate CAN signals by a maximum of 0.42%—well within the safety tolerances of drive-by-wire vehicles.
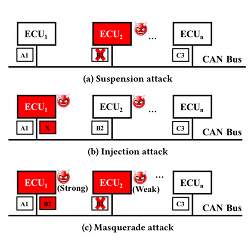
The Transmitter Authentication capability appended to the CAN (TACAN) was explained in detail in the paper TACAN: Transmitter Authentication through Covert Channels in Controller Area Networks. According to the paper, covert channels are capable of enforcing transmitter authentication, securing drive-by-wire automobiles from injection attacks (which infect a single ECU to send phony messages) or suspension attacks (which delete messages from a single ECU), as well as more sophisticated combinations of these, such as masquerade attacks (which infect two ECUs) and Denial of Service (DoS) attacks (which flood the bus with more messages than it can handle).
Conventional security protocols can be programmed into the firmware of the ECUs (adding to its traffic management overhead), but by using the covert channels instead, the original ECU protocols remain unchanged, which means there is no added overhead, no extra bits or messages, and no timing changes, since the complete security protocol runs outside the original-equipment ECUs using hacker-like covert channels.
Use of the covert channels for authentication purposes, however, does rely on the addition of a trusted monitor unit and a tamper-resistance memory.
"The key novelty of TACAN is that it exploits covert channels for transmitting the authentication information, which effectively avoids introducing traffic overheads or increasing the bus load," said Ying. "The basic idea of a TACAN is to have each ECU transmit unique authentication information as digital fingerprints. By verifying the authentication information with a trusted monitor node we avoid malicious ECU messages that attempt attacks."
The authenticity of a message is verified by a secure key stored in the tamper-resistant memory. The resulting transmitter authentication securely identifies the source of each command issued on the CAN, and only accepts those coming from the manufacturer's original equipment.
The researchers say they verified their system by installing it on the University of Washington's EcoCAR, which competes in the U.S. Department of Energy (DoE) Advanced Vehicle Competitions. The demonstration tests showed that the covert channels authenticated all messages sent from original-equipment ECUs, blocked attacks, kept error rates within nominal bounds, and added no traffic overheads to the CAN.
Three covert channels used by hackers to send malicious messages were each implemented on the EcoCAR, to test its effectiveness against known hacking techniques.
The first utilized the Inter-Arrival Time (IAT) technique, which squeezes extra bits between the inter-transmission time (ITT) of CAN messages. These extra bits transmit all the authentication traffic, allowing valid messages to use the CAN as usual, but blocking all non-authentic messages inserted by hacks. Using the IAT covert channel added just 0.1% bit-error rate, which is well within acceptable limits, according to the researchers.
The second covert channel tested on the EcoCAR used a CAN clock offset-based exploit, which accumulates clock deviations to differentiate the modulated samples from the noise between messages. Similar to the IAT method, the offset-based exploit used the nominal period of targeted messages, then computed the observed clock offset as the difference between the expected elapsed time at the transmitter and the actual elapsed time at the receiver. As a result, like the IAT method, it sent its bits between valid messages, but with a 0.42% bit-error rate which is also within acceptable limits, according to the researchers.
The third covert channel used the least-significant bit of CAN bus numeric transmissions, which slightly degraded the dynamic range of those numbers, but was the most bit-error free, since the bit-error rate of the LSB-based covert channel was equal to that of the normal CAN bus, at 0.00000031%
The researchers said future work on the technology will aim to minimize the error rates further by using a combination of covert channels simultaneously.
R. Colin Johnson is a Kyoto Prize Fellow who has worked as a technology journalist for two decades



Join the Discussion (0)
Become a Member or Sign In to Post a Comment