When the crew of an $80-million super-yacht in the Ionian Sea checked its computer, they realized they were drifting slightly off course, likely as a result of strong currents buffeting their ship. The crew made adjustments and went back to work—without realizing they were now taking directions from a hacker.
In the bowels of the ship, Todd Humphreys, an associate professor in the Department of Aerospace Engineering and Engineering Mechanics at the University of Texas at Austin, worked with his team to feed the super-yacht’s crew false navigation data using a few thousand dollars worth of hardware and software.
The crew was completely unaware they were now piloting in a direction of Humphreys’ choosing.
Thankfully, it was all an experiment that took place with the yacht owner’s blessing. If it had been real, Humphreys could have sent the superyacht 1,000 miles off-course into the hands of a rogue government, terrorist group, or professional criminal organization—and the crew would not have realized it until it was far too late.
Welcome to the very real dangers posed by Global Positioning System (GPS) spoofing, or the dark art of convincing computers you are somewhere that you’re not. It is surprisingly easy—and shockingly dangerous, because we’re not prepared for it at all.
GPS Is Easy to Spoof
The U.S. Global Positioning System consists of 24 satellites that orbit Earth. GPS devices receive signals from the nearest satellites that allow them to determine their precise location, whether you’re looking for creatures in the wildly popular Pokémon Go app, or going to war in a billion-dollar battleship. A range of GPS devices and networks are used for everything from military applications to commercial needs—and all the use cases in between.

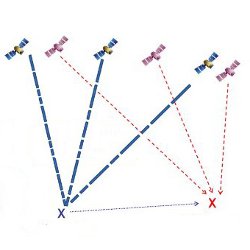
Figure. Part of an animation showing how a radio navigation research team from The University of Texas at Austin was able to successfully spoof the GPS system of an $80-million private yacht.
Yet all of these systems rely on the data from the network of GPS satellites. If you can corrupt the data coming from those satellites, you can create a world of headaches for systems that rely on this data.
GPS spoofing can be performed with relatively low-cost tech, which is an expensive problem for the people, companies, and governments that trust the system implicitly. In the case of Humphreys’ superyacht hacking, he and his team used about $2,000 worth of tech. Even in more advanced spoofing scenarios, the technology is still straightforward, says Dinesh Manandhar, an associate professor and GPS expert at the University of Tokyo.
“A device that can generate GPS signals is necessary. Such devices are available from GPS signal simulator device manufacturers,” Manandhar explains. These devices are used to test GPS receivers in factories. As such, they can be programmed to transmit a signal that makes receivers behave any way you like.
“So far as I know, no commercial GPS receivers offer any strong defense against spoofing or even any reliable spoofing detection capability,” says Humphreys.
Stealing an $80-Million Superyacht
In 2013, Humphreys, then a researcher in the Department of Aerospace Engineering and Engineering Mechanics at the Cockrell School of Engineering, was invited, along with a team of students, aboard an $80-million yacht in the Ionian Sea to test their GPS spoofing technology. Using his hardware and software rig, Humphreys managed to falsify GPS data used by the ship, effectively giving him control over the vessel.
Humphreys explained GPS receivers calculate their distance from several satellites at the same time. Each satellite has a code—called a pseudorandom noise (PRN) code—that identifies which satellite in the GPS network is broadcasting. Humphreys’ spoofing equipment slowly replaced the real GPS signals with fake ones, working delicately so the ship’s system did not detect an abrupt change in signal.
The spoofed GPS reported the yacht was three degrees off-course. The crew, unaware when the experiment would take place, adjusted the ship’s course based on the spoofed GPS. The crew assumed it was due to natural forces such as water currents and crosswinds.”
GPS spoofing can be used for all sorts of nefarious purposes. As seen with the yacht, cargo shipments are at risk, especially dangerous or high-value ones that are required to follow designated GPS routes. Geofences—or digitally proscribed boundaries—are used to protect sensitive data in many corporations; GPS spoofing could be used to access that data well out of the bounds intended.
Once you add emerging technologies, like self-driving cars, to the mix, it gets even scarier. Autonomous vehicles use GPS data at regular intervals not only to understand where they are, but also to decide where to drive passengers and cargo.
Humphreys’ yacht spoofing was the first time commercial tech had been used in such an effective—and powerful—demonstration.
Now, said Manandhar, it is even easier to acquire spoofing technology. “Recently, software-based low-cost devices have become available that cost less than $1,000.”
A Problem for Governments, People
It is not just yacht owners who need to be concerned; the problem is especially acute for national governments and international bodies, which are waking up to the dangers posed by GPS spoofing.
Incredibly, Europe’s Galileo global navigation satellite system—the European Union’s version of GPS—operated beginning in December 2016 “with no way to protect civilian users from hacking attempts,” reported ZDNet.
University of Leuven researchers Ashur and Rijmen say they have developed an authentication protocol to deter the forging of Galileo’s navigation data.
The protocol, called the TESLA signature, is designed to complement location data with a cryptographic “signature,” so Galileo’s satellites would send both navigation data and the cryptographic signature to the receiving client. The client would not trust the data right away; only when the signature was verified would the client use the GPS data it had received.
“Using cryptography makes it hard to forge a signature, such that even an adversary that can feed the client with false data cannot forge a signature, thus the client does not use forged data,” Ashur says.
This would prevent, say, spoofing the signal to hijack a self-driving car or reroute a drone that relied upon the data.
However, the Galileo system, which comes fully online in 2020, presented a unique obstacle: low bandwidth. Galileo has relatively low-bandwidth signals that make a typical approach to the problem, using public-key cryptography, impossible.
“The uniqueness of our solution is that it uses symmetric cryptography and can thus fit into the bandwidth constraints,” says Ashur. The protocol is scheduled to go into effect in 2018, according to ZDNet. Until all 24 of Galileo’s satellites are deployed and operational in 2020, however, the protocol will “operate in test mode.”
In the meantime, manufacturers are starting to pay attention to the problem, says Humphreys. Some, like u-blox, a Swiss company that creates wireless semiconductors and modules for consumer, automotive, and industrial markets, offer anti-spoofing measures such as the capability to detect fake global navigation satellite system (GNSS) signals, as well as a message integrity protection system to prevent “man in the middle” attacks.
Humphreys also points to the U.S. Department of Homeland Security’s recent document on anti-spoofing, “Improving the Operation and Development of Global Positioning System (GPS) Equipment Used by Critical Infrastructure,” as a sign that the right parties are taking GPS spoofing seriously.
Manandhar has developed anti-spoofing methodologies for Japanese satellites that may be used in the next generation to be sent into orbit, he says. He recommends that major navigation data provider countries like the U.S., Japan, the European Union, China, and India conduct official joint discussions on the security of their systems at the International Committee on Global Navigation Satellite Systems, an organization under the umbrella of the United Nations.
Cargo shipments are at risk from GPS spoofing, as are geofences—digitally proscribed boundaries used by many corporations to protect sensitive data.
The dangers, however, are not going away. Humphreys worries particularly that spoofing the GPS-sourced timing used to regulate financial databases could create havoc. Industries like financial services, he says, “have backups in place, but on close inspection one realizes that the backups themselves are either short-term or eventually trace their source to GPS.”
“A coordinated attack that understood the finance world’s dependency on GPS would be hard to detect and even harder to defeat,” he cautions.
Psiaki, M., and Humphreys, T.
Protecting GPS from Spoofers Is Critical to the Future of Navigation, IEEE Spectrum, Jul 29, 2016, http://spectrum.ieee.org/telecom/security/protecting-gps-from-spoofers-is-critical-to-the-future-of-navigation
Amirtha, T.
Satnav spoofing attacks: Why these researchers think they have the answer, ZDNet, Mar 27, 2017, http://www.zdnet.com/article/satnav-spoofing-attacks-why-these-researchers-think-they-have-the-answer/
U.S. Department of Homeland Security, National Cybersecurity & Communications Integration Center, National Coordinating Center for Communications Improving the Operation and Development of Global Positioning System (GPS) Equipment Used by Critical Infrastructure, http://bit.ly/2oZewfz




Join the Discussion (0)
Become a Member or Sign In to Post a Comment